The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent alert concerning a newly disclosed security flaw in…
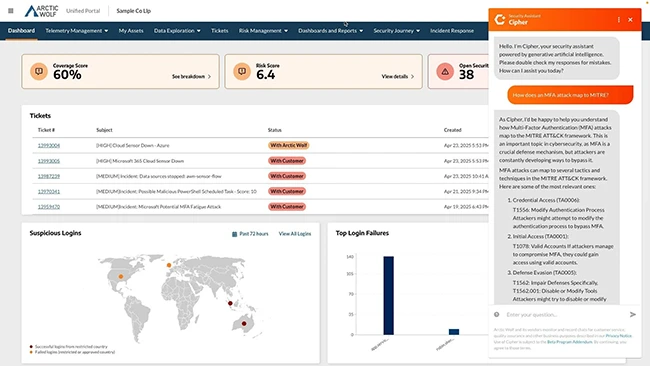
Arctic Wolf has introduced Cipher, an AI security assistant that provides customers with self-guided access to deeper security insights directly…
U.S. CISA adds Qualitia Active! Mail, Broadcom Brocade Fabric OS, and Commvault Web Server flaws to its Known Exploited Vulnerabilities…
The Cybersecurity and Infrastructure Security Agency (CISA) has added the Commvault Web Server vulnerability (CVE-2025-3928) to its Known Exploited Vulnerabilities…
A newly disclosed vulnerability in the Linux kernel, tracked as CVE-2025-21756 and dubbed “Attack of the Vsock,” has sent ripples through the…
In the ever-evolving landscape of cybersecurity, new types of threats are constantly emerging. One relatively new tactic that has been…
Cloudflare says it mitigated 20.5 million DDoS attacks in the first quarter of 2025. This is a 358% increase compared…
Apr 29, 2025Ravie LakshmananCybersecurity / Malware In a new campaign detected in March 2025, senior members of the World Uyghur…
By Salleh Kodri, SE Regional Manager, Cyble 2024 wasn’t just another year in Malaysia’s digital journey — it was a wake-up…
The Apache Software Foundation disclosed a significant security vulnerability in Apache Tomcat that could allow attackers to bypass security rules…
A recent surge in cyber reconnaissance has put thousands of organizations at risk after GreyNoise, a global threat intelligence platform,…
When someone asks how you start a typical weekday, your answer likely includes the usual suspects, be it waking up,…