Hitachi Vantara, a subsidiary of Japanese multinational conglomerate Hitachi, was forced to take servers offline over the weekend to contain…
A newly analyzed Python-based Remote Access Trojan (RAT) has emerged as a significant cybersecurity threat, utilizing Discord as its command-and-control…
Fujitsu UK is rewarding staff for meeting a sales threshold, in further evidence that the company’s gesture to pause bidding…
The FBI’s Internet Crime Complaint Center (IC3) has reported a record-breaking loss of $16.6 billion (approximately ₹1.38 lakh crore) due…
Offensive Security warned Kali Linux users to manually install a new Kali repository signing key to avoid experiencing update failures….
The NSFOCUS Fuying Laboratory’s global threat hunting system identified 19 sophisticated Advanced Persistent Threat (APT) attack campaigns, predominantly targeting regions…
BreachForums posts a PGP-signed message explaining the sudden April 2025 shutdown. Admins cite MyBB 0day vulnerability impacting the site, plan…
A trusted tool has turned traitor. A new Citizen Lab investigation reveals that UyghurEditPP, a legitimate open-source Uyghur-language text editor,…
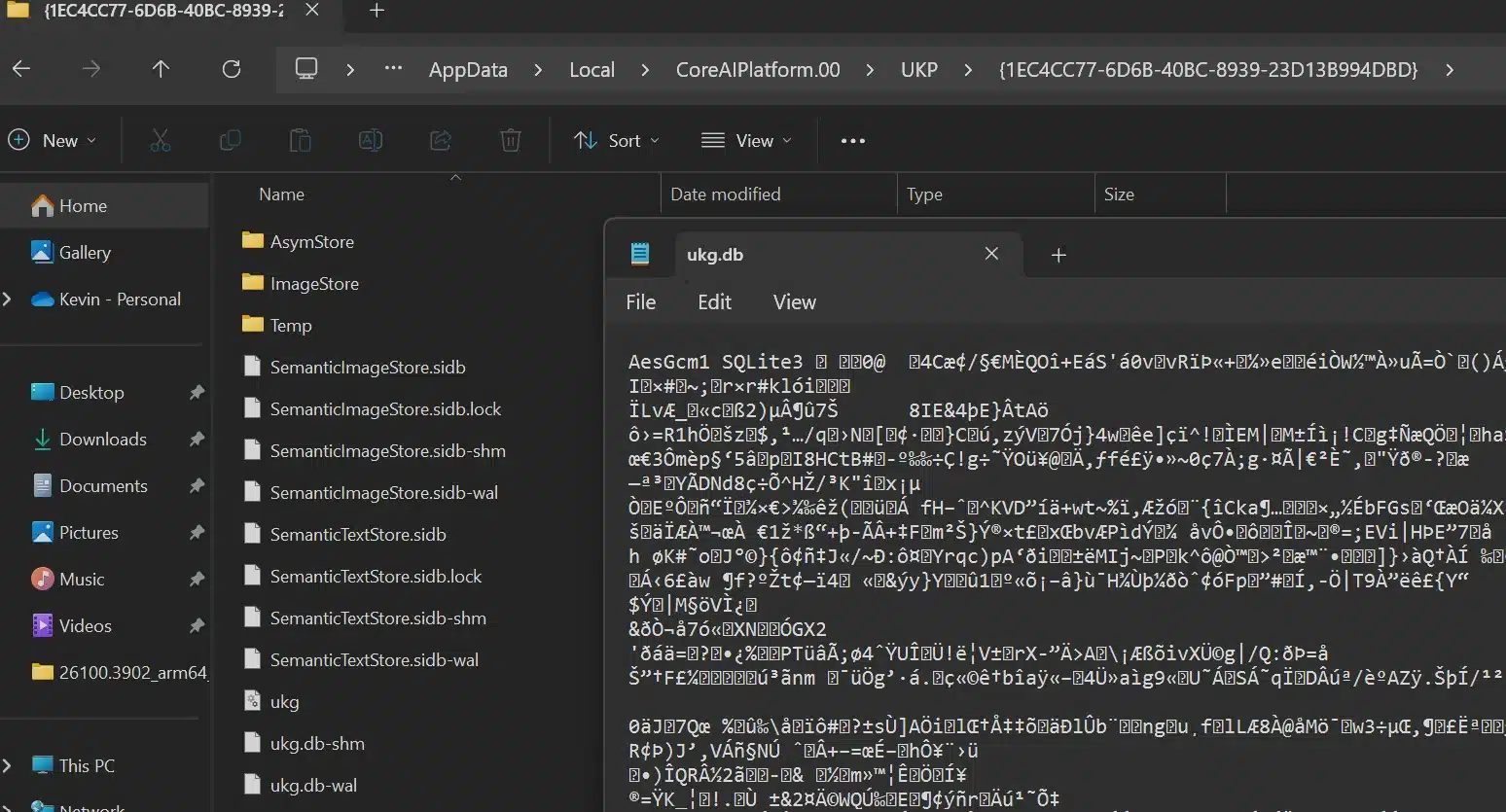
Nearly a year after its troubled initial rollout, Microsoft Recall is back. Microsoft announced in an April 25 blog post…
I’m still running daily, but I’ve swapped some days for walking with a weighted vest. The main limitation I’m currently…
Employee benefits administration firm VeriSource Services is warning that a data breach exposed the personal information of four million people. …
The eSentire’s Threat Response Unit (TRU) in early March 2025, a sophisticated cyberattack leveraging SocGholish malware, also known as FakeUpdates,…