Darcula phishing platform adds AI to create multilingual scam pages easily. Netcraft warns of rising risks from Darcula-Suite upgrade. Cybersecurity…
Flashpoint announced new capabilities to its flagship platform, Flashpoint Ignite. These innovations are designed to deliver insights that align with…
Cybersecurity has rapidly evolved from a back-office technical concern to a boardroom imperative. As digital transformation accelerates and organizations embrace…
China has accused U.S. intelligence agencies of carrying out a sophisticated cyberattack against one of its foremost commercial cryptography providers,…
Two individuals have been arrested in a joint international operation dismantling JokerOTP, a sophisticated phishing tool used to intercept 2FA…
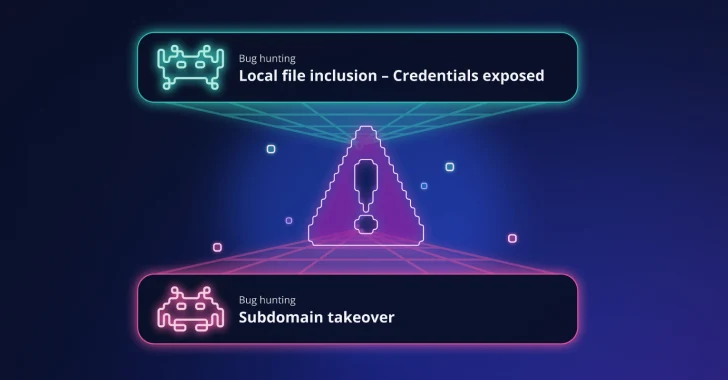
Not every security vulnerability is high risk on its own – but in the hands of an advanced attacker, even…
The UK could save £200bn if the workforce adopts artificial intelligence (AI) to improve productivity. That is the headline finding…
What is also clear from the documents is that US police are aware of the control corporations have over their…
A security researcher has uncovered a critical vulnerability in iOS, Apple’s flagship mobile operating system. The flaw, CVE-2025-24091, which leverages…
PoC rootkit Curing evades traditional Linux detection systems Pierluigi Paganini April 28, 2025 Researchers created a PoC rootkit called Curing…
Why Application Security is Non-Negotiable The resilience of your digital infrastructure directly impacts your ability to scale. And yet, application…
CVE-2025-31324, a critical vulnerability in the SAP NetWeaver platform, is being actively exploited by attackers to upload malicious webshells to…