A recently disclosed data breach at Coinbase has been linked to India-based customer support representatives from outsourcing firm TaskUs, who threat…
A decade-old critical security vulnerability has been discovered in Roundcube Webmail that could allow authenticated attackers to execute arbitrary code…
The manufacturing sector has emerged as a prime target for cyber attackers in 2024, with a staggering 71% surge in…
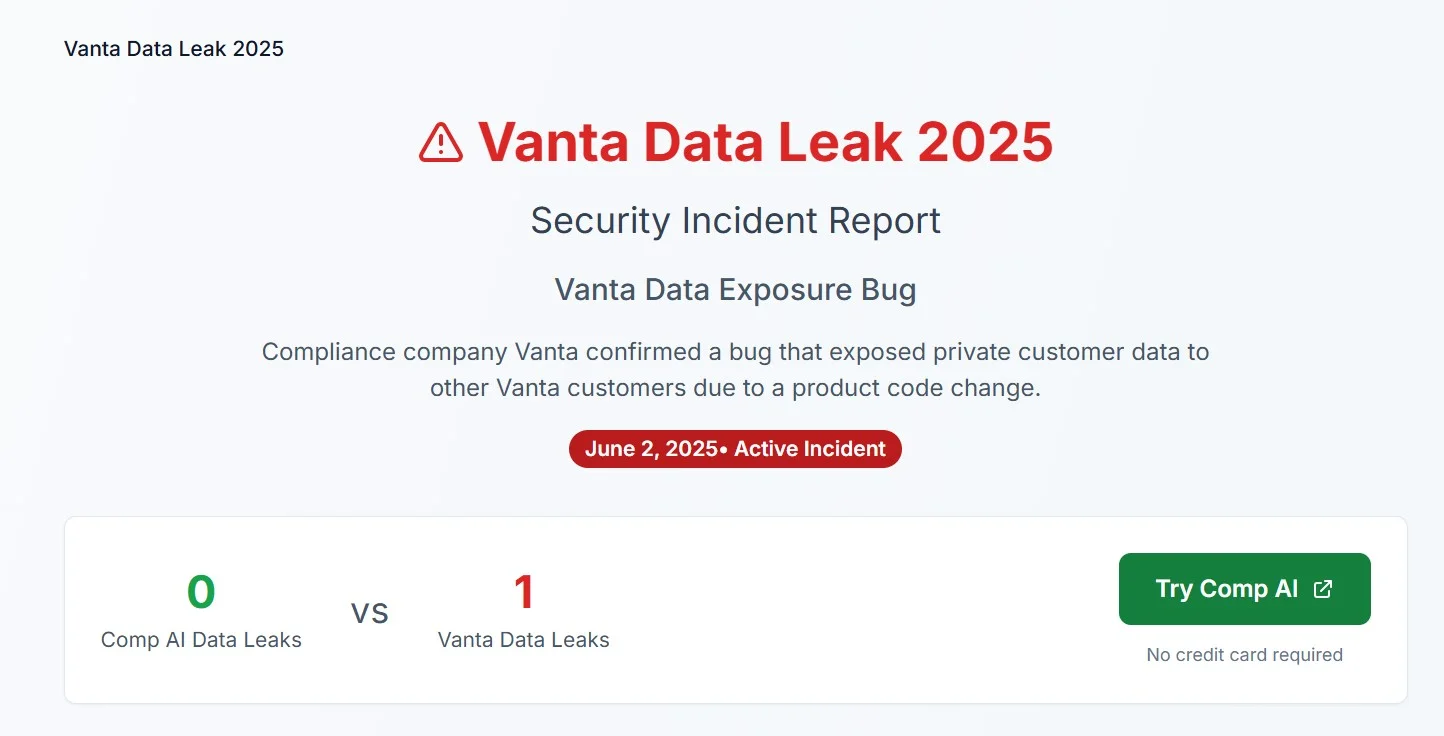
Compliance automation provider Vanta confirms a software bug exposed private customer data to other users, impacting hundreds of clients. Learn…
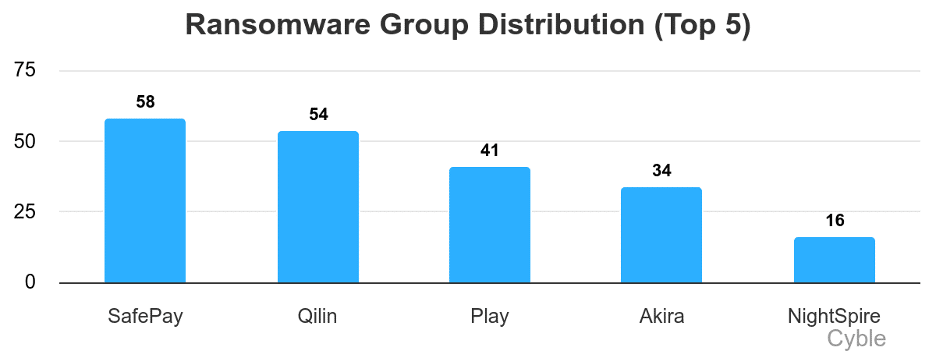
SafePay’s journey to the top of the ransomware leaderboard was a quick one. The SafePay ransomware group first emerged in…
The UK’s 2025 Strategic Defence Review (SDR) details a plan to integrate its military defensive and offensive capabilities through increased…
CrowdStrike and Microsoft announced an agreement Monday to formally connect the different names each company uses for the same threat…
Two malicious RubyGems packages posing as popular Fastlane CI/CD plugins redirect Telegram API requests to attacker-controlled servers to intercept and…
As cybercrime costs surge toward an estimated $10.5 trillion annually by 2025, Chief Information Security Officers (CISOs) are stepping out…
Hundreds of emails and internal documents reviewed by WIRED reveal top lobbyists and representatives of America’s agricultural industry led a…
Cybersecurity researchers have shed light on the often-underestimated vulnerabilities in containerized environments, emphasizing the critical role of host-based log analysis…
Modern software development demands rapid delivery of high-quality applications that can adapt to changing business requirements and user expectations. Continuous…