Shadow Servers have identified 454 SAP NetWeaver systems vulnerable to a critical zero-day vulnerability that has been actively exploited in…
A large-scale phishing campaign targets WooCommerce users with a fake security alert urging them to download a “critical patch” that adds a…
Melbourne Airport is building up its cyber detection and response capabilities in order to secure 30 million annual passenger journeys,…
The ransomware scene is re-organizing, with one gang known as DragonForce working to gather other operations under a cartel-like structure….
Brave has open-sourceed a new tool called “Cookiecrumbler,” which uses large language models (LLMs) to detect cookie consent notices and…
Coinbase has fixed a confusing bug in its account activity logs that caused users to think their credentials were compromised….
As we usher in a new year, it’s crucial to focus on key areas in cybersecurity that demand our attention….
NoSQL injections are relatively easier to exploit than classic SQL injections. However, developers often overlook these vulnerabilities, mainly due to…
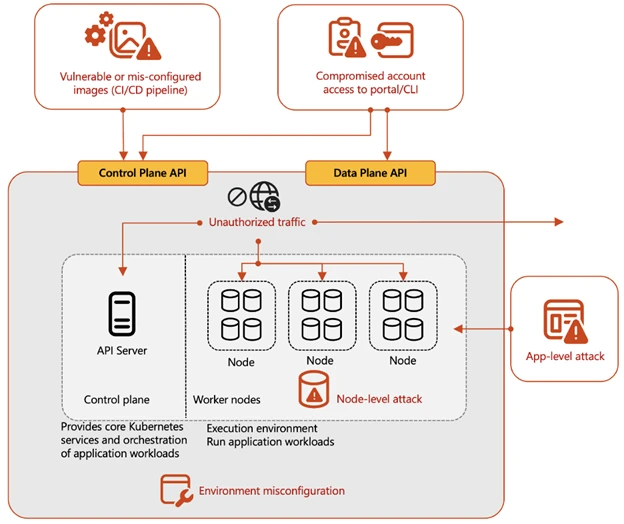
Storm-1977 targets education sector with password spraying, Microsoft warns Pierluigi Paganini April 27, 2025 Microsoft warns that threat actor Storm-1977…
The holiday season is a time for joy, celebration, and, unfortunately, an uptick in cyber threats. From phishing scams that…
In the ever-changing world of cybersecurity, organizations are constantly challenged to choose the right security operations model that best supports…
In an era where digital identities have become the primary attack vector, CISOs face unprecedented pressure to secure access across…