A sophisticated phishing campaign dubbed “Power Parasites” has been actively targeting global energy giants and major brands since 2024, according…
Extended Detection and Response (XDR) has emerged as a transformative security technology that unifies visibility across multiple security layers. When…
In the ever-evolving world of cybersecurity, organizations must continuously adapt their defense strategies to stay ahead of increasingly sophisticated threats….
A critical vulnerability (CVE-2025-31324) in SAP NetWeaver Visual Composer puts systems at risk of full compromise. Learn how to check…
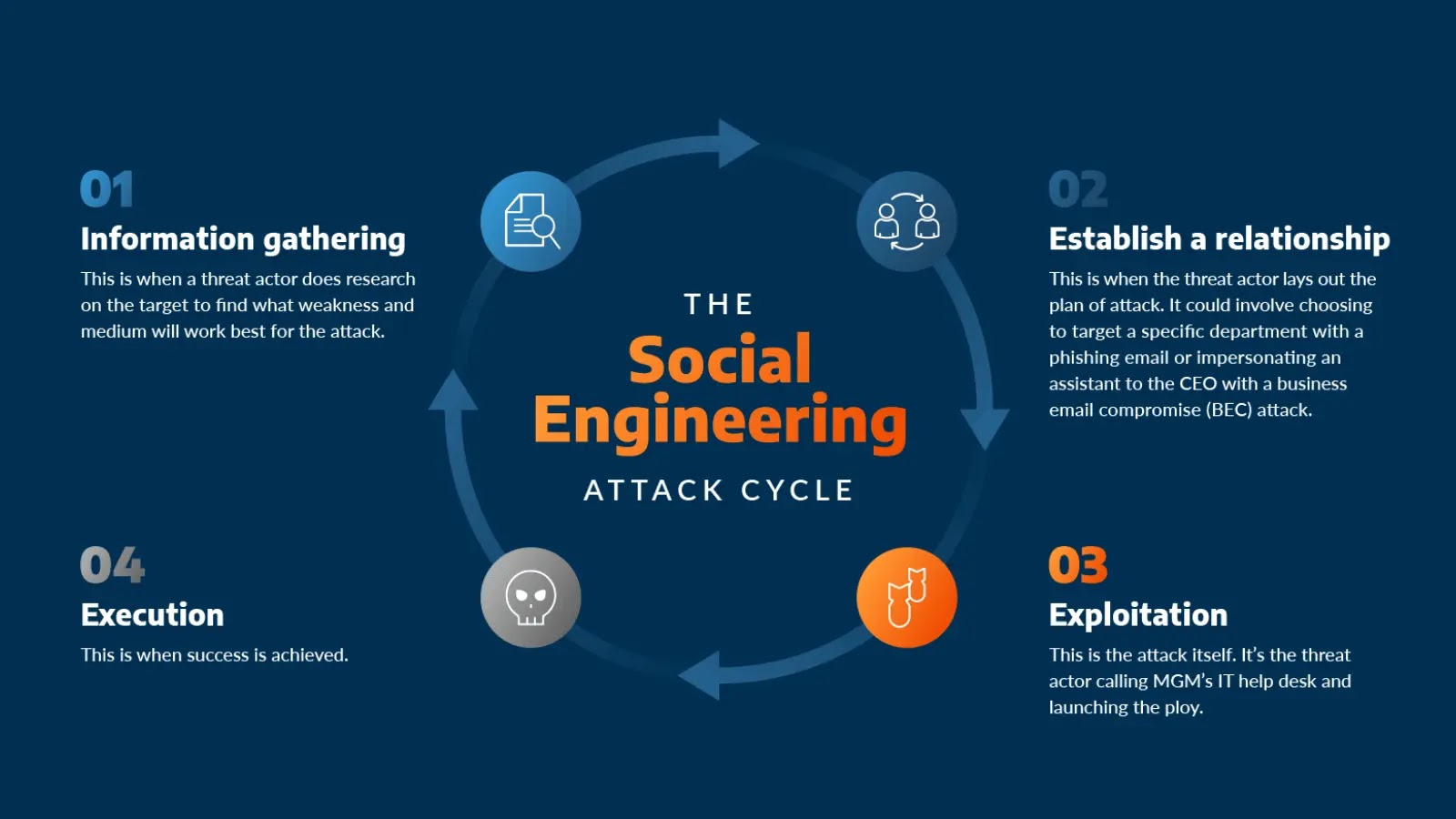
Social engineering has become the dominant attack vector in the modern cybersecurity landscape. As technical defenses evolve and strengthen, attackers…
The cybersecurity landscape has changed dramatically in recent years, largely due to the introduction of comprehensive data protection regulations across…
Apr 26, 2025Ravie LakshmananMalware / Vulnerability Cybersecurity researchers have detailed the activities of an initial access broker (IAB) dubbed ToyMaker…
As the world becomes increasingly reliant on digital infrastructure, data centers have evolved into the backbone of business operations, cloud…
As the Trump administration’s aggressive immigration policy ramps up, people have started to seriously consider their privacy and security when…
CEO of cybersecurity firm charged with installing malware on hospital systems Pierluigi Paganini April 26, 2025 Veritaco CEO Jeffrey Bowie…
Developing a strong security culture is one of the most critical responsibilities for today’s CISOs (Chief Information Security Officers) and…
A concerning large-scale phishing campaign targeting WooCommerce users has been uncovered by the Patchstack securpity team, employing a highly sophisticated…