Software development is about to undergo a generative change. What this means is that AI (Artificial Intelligence) has the potential…
Microsoft has released the KB5055627 preview cumulative update for Windows 11 24H2 with many new features gradually rolling out, and some…
Silent Push Threat Analysts have uncovered a chilling new cyberattack campaign orchestrated by the North Korean Advanced Persistent Threat (APT)…
Enterprises using Commvault Innovation Release are urged to patch immediately against CVE-2025-34028. This critical flaw allows attackers to run code…
This morning I tweeted: “Most people don’t actually know what’s ‘best’ for themselves.” And atomiczsec replied and said “How do…
Two vulnerabilities impacting Craft CMS were chained together in zero-day attacks to breach servers and steal data, with exploitation ongoing, according…
Researchers from Unit 42 have uncovered a massive wave of SMS phishing, or “smishing,” activity targeting unsuspecting users. Since the…
A bipartisan trio of House lawmakers is pushing a bill that would give law enforcement more resources to tackle financial…
Silent Push Threat Analysts have uncovered a widespread phishing and scam operation dubbed “Power Parasites,” targeting prominent energy companies and…
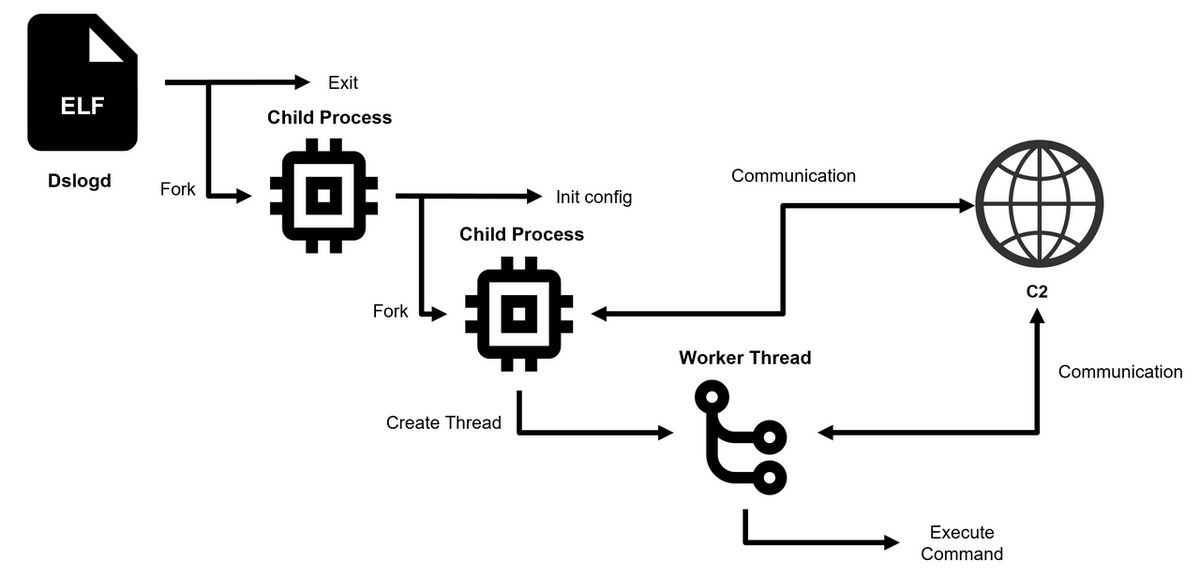
JPCERT warns of DslogdRAT malware deployed in Ivanti Connect Secure Pierluigi Paganini April 25, 2025 Researchers identified a new malware,…
Secureworks Counter Threat Unit (CTU) researchers have uncovered innovative strategies deployed by the DragonForce and Anubis ransomware operators in 2025….
Threat hunters and security researchers have observed widespread exploitation of a zero-day vulnerability affecting SAP NetWeaver systems. The unrestricted file…