Organizations have implemented various aspects of threat exposure validation, including security control validation (51%) and filtering threat exposures based on…
With credit card skimming crimes escalating nationwide, the U.S. Secret Service’s Washington Field Office is sharing essential tips for the…
In a bold move to protect user privacy, Apple Inc. has issued a warning to its vast user base of…
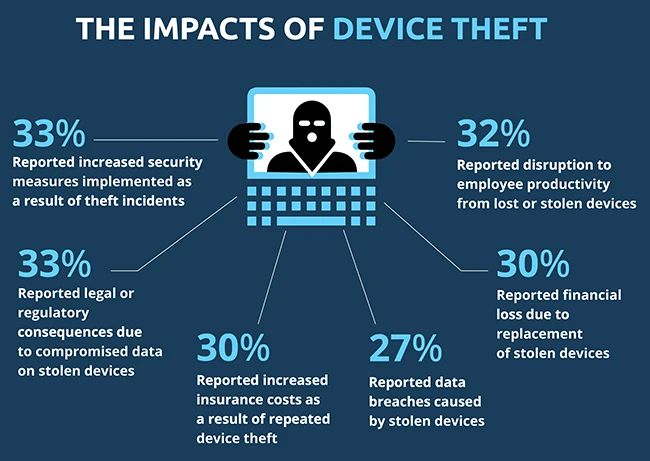
76% of respondents have been impacted by incidents of device theft in the past two years, with incidents more common…
The new ETSI TS 104 223 specification for securing AI provides reliable and actionable cybersecurity guidance aimed at protecting end…
Here’s a look at the most interesting products from the past week, featuring releases from Bitdefender, PowerDMARC, Skyhawk Security, Stellar…
North Korean cyber spies created two businesses in the US, in violation of Treasury sanctions, to infect developers working in…
Attackers exploited nearly a third of vulnerabilities within a day of CVE disclosure in the first quarter of 2025, VulnCheck…
The Cybersecurity and Infrastructure Security Agency will soon have a new second-in-command. Madhu Gottumukkala has been named deputy director. He…
Two federal cybersecurity officials said Thursday that they’re using — or contemplating using — artificial intelligence to conduct tasks that…
Cybercriminals are increasingly weaponizing Scalable Vector Graphics (SVG) files to orchestrate sophisticated phishing campaigns. According to research from Intezer, a…
China-backed actors “stand out” in threatening America’s energy infrastructure and could disrupt the country’s power networks in the event of…