NVIDIA has issued an urgent security advisory addressing three high-severity vulnerabilities in its NeMo Framework, a platform widely used for…
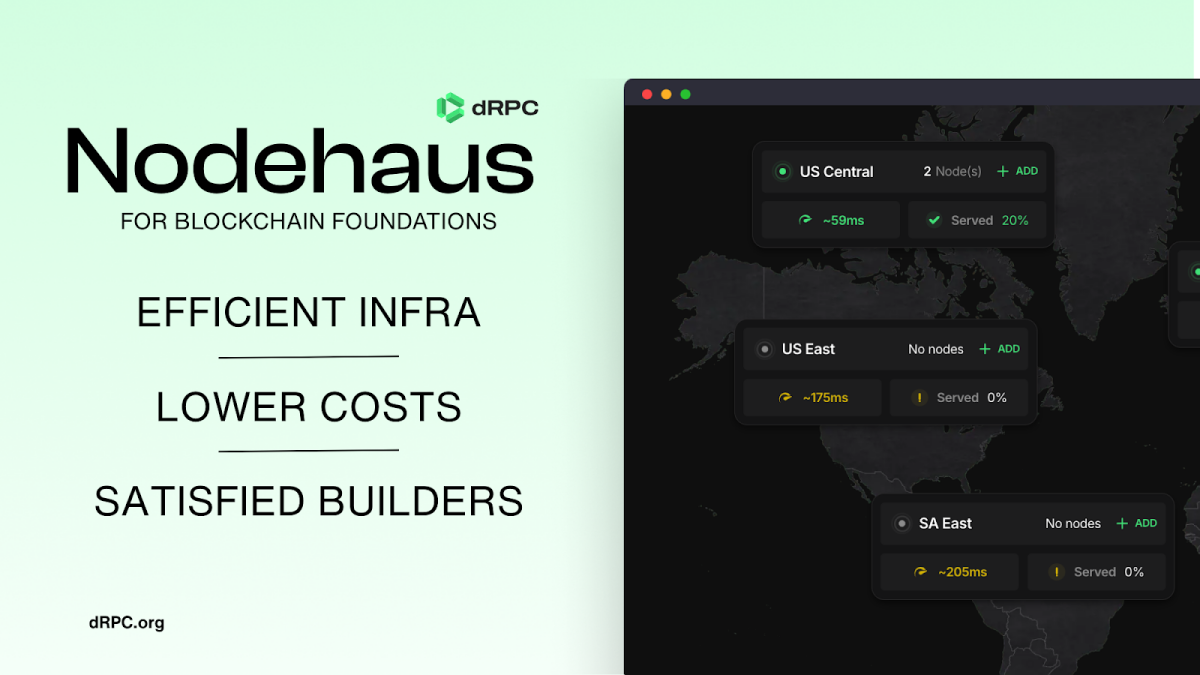
Blockchain infrastructure provider dRPC has announced the launch of a NodeHaus platform that enables chain foundations unprecedented control over their…
Got an Android phone? Got a tap-to-pay card? Then you’re like millions of other users now at risk from a…
Apr 24, 2025Ravie LakshmananEndpoint Security / Linux Cybersecurity researchers have demonstrated a proof-of-concept (PoC) rootkit dubbed Curing that leverages a…
Organisations holding data on US citizens must do more to address gaps in their cyber security posture and respond to…
Abstract In the age of information, where the line between reality and fiction is increasingly blurred, deepfake technology has emerged…
Cisco has issued a high-severity advisory (cisco-sa-erlang-otp-ssh-xyZZy) warning of a critical remote code execution (RCE) vulnerability in products using Erlang/OTP’s…
SessionShark phishing kit bypasses Office 365 MFA by stealing session tokens. Experts warn of real-time attacks via fake login pages…
24 Apr Cybercrime Magazine’s First YouTube Video: A 60-Second Walk In The Park Posted at 08:33h in Blogs by Taylor…
If your organization is using Commvault Command Center for your data protection, backup creation, configuration and restoration needs, you should…
Apr 24, 2025Ravie LakshmananVulnerability / Threat Intelligence As many as 159 CVE identifiers have been flagged as exploited in the…
Since the government announced in the King’s speech last year that they would bring forward a Cyber Security and Resilience…