Crooks exploit the death of Pope Francis Pierluigi Paganini April 24, 2025 Crooks exploit the death of Pope Francis, using…
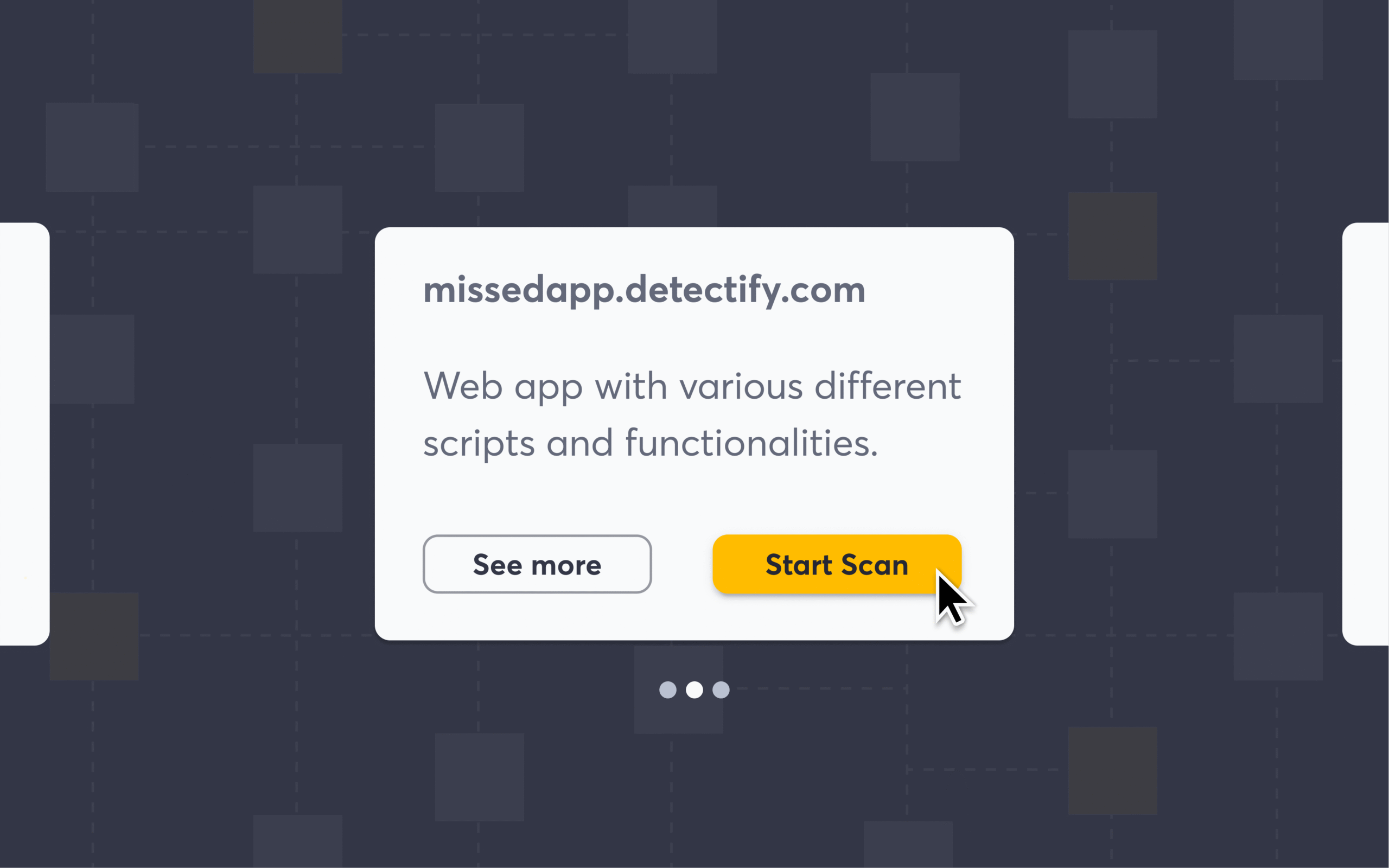
As 9 out of 10 valuable web apps are missing testing, we’re launching new capabilities to help teams know what…
Enterprises and managed service providers globally are now facing urgent security concerns following the disclosure of a major pre-authenticated remote…
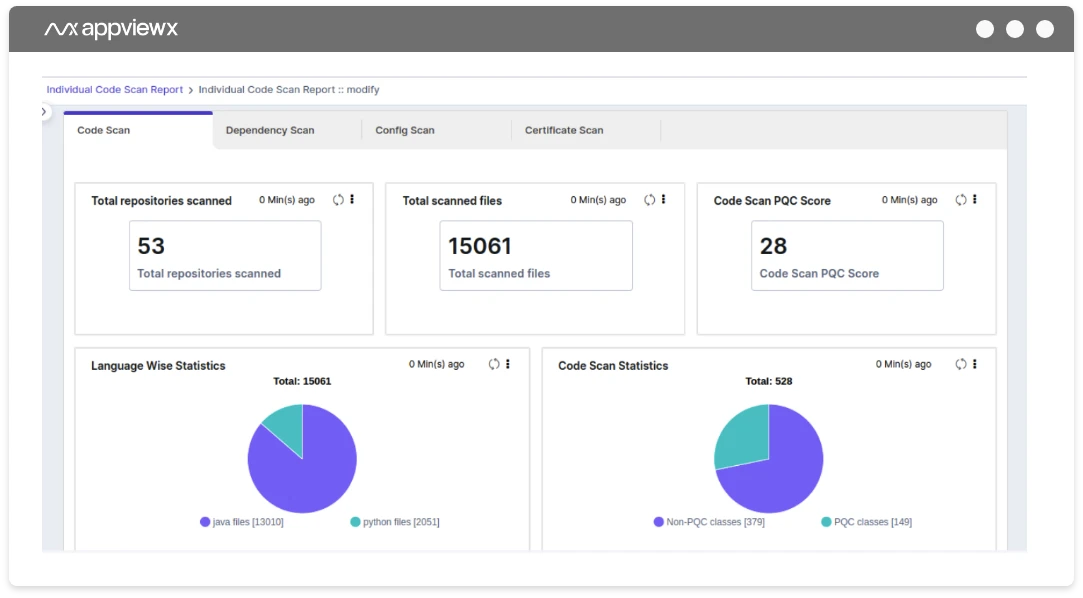
AppViewX has announced the launch of the AVX ONE Post-Quantum Cryptography (PQC) Assessment Tool that generates a Cryptographic Bill of…
Apr 24, 2025Ravie LakshmananPhishing / Cybercrime The threat actors behind the Darcula phishing-as-a-service (PhaaS) platform have released new updates to…
In this podcast, we talk to Mathieu Gorge, CEO of Vigitrust, about the ongoing impact of artificial intelligence (AI) on…
A new wave of attacks targeting Ivanti Connect Secure VPN devices has revealed a stealthy malware strain known as DslogdRAT,…
Chinese artificial intelligence startup DeepSeek has come under intense scrutiny from South Korean authorities for allegedly transferring user data and…
A significant security gap in Linux runtime security caused by the ‘io_uring’ interface allows rootkits to operate undetected on systems…
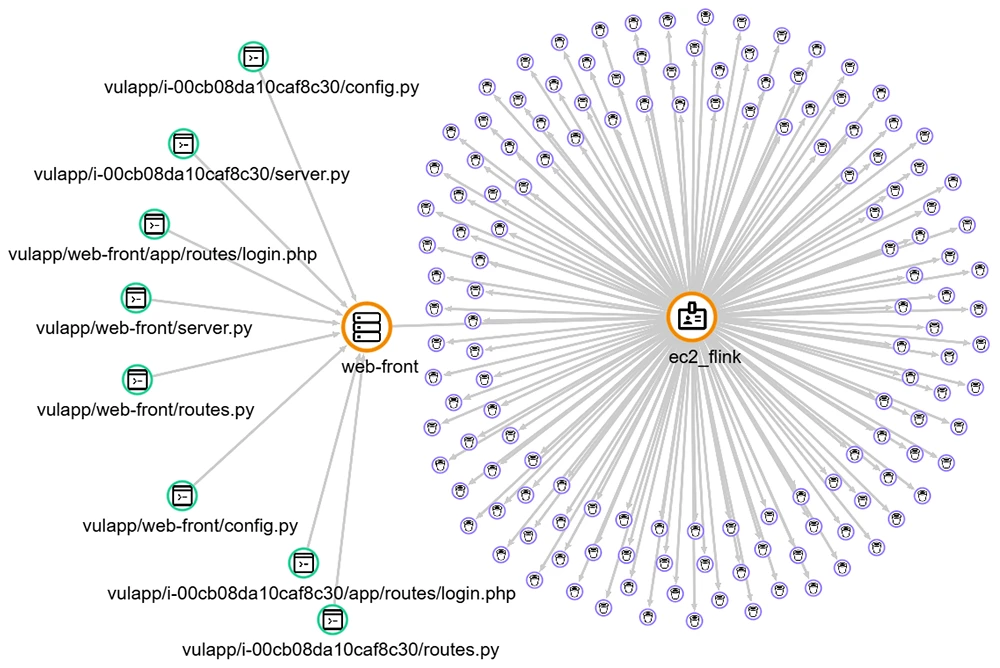
Security researcher Alessandro Sgreccia (aka “rainpwn”) has revealed a set of critical vulnerabilities in Zyxel’s USG FLEX-H firewall series that…
With the rise of fintechs, accuracy alone isn’t enough, security and reliability are just as necessary. For fintech companies and…
Skyhawk Security is adding new protection for custom-built cloud applications. The company announced the update to its AI-powered Autonomous Purple…