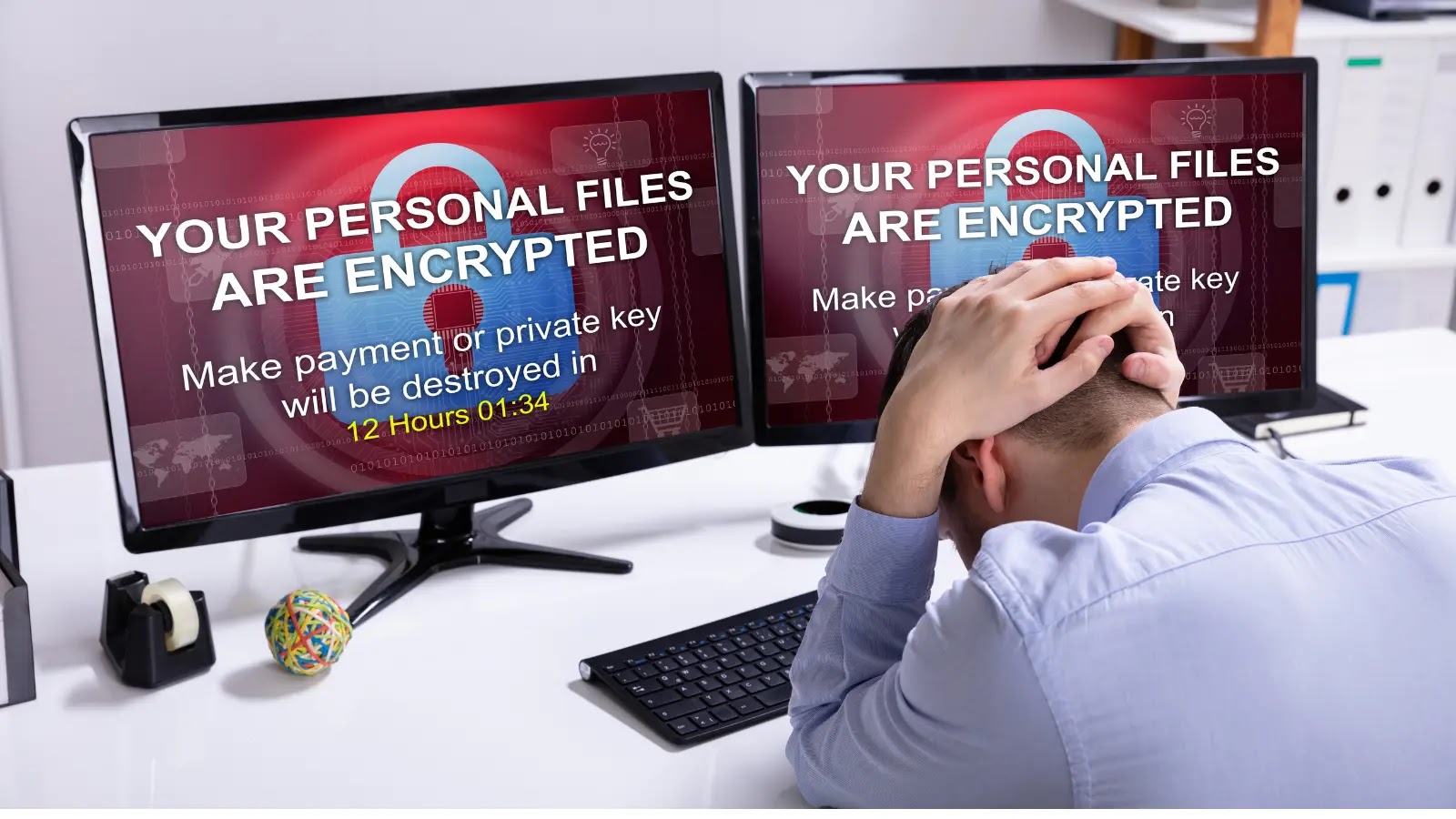
Ransomware attacks have entered a new era of sophistication and danger, with AI-powered ransomware attacks marking a significant evolution beyond…
In an era where cyber threats continuously evolve and traditional security perimeters become obsolete, Zero Trust Architecture for 2025 has…
As we navigate through 2025, cybersecurity professionals face an increasingly sophisticated threat landscape. Network Intrusion Detection Systems (IDS) have become…
How to make plugin Create a new repository using the Caido’s starterkit-plugin GitHub template feature. Then, you can install dependencies…
As data breaches continue to make headlines and regulatory penalties reach record highs, organizations face mounting pressure to strengthen their…
ZAP 2.15가 릴리즈되었습니다. OWASP를 나오는 이슈로 인해 2.14가 빠르게 출시됬던 상태라 2.15까지의 기간 또한 짧았네요. 오늘은 2.15 버전에 대해 빠르게…
In an era where data breaches and privacy violations continue to make headlines, organizations worldwide face increased pressure to implement…
Optimizing Security Tests with Match and Replace in Burp/Caido/ZAP 최근에 저는 Burpsuite, Caido, ZAP을 모두 사용하고 있습니다. 기존 환경에서 Caido가…
Recent data reveals that real-time endpoint threat detection powered by AI-enhanced behavioral monitoring is becoming the cornerstone of modern cybersecurity…
Harmoniously Combining Warp Themes and Vim Themes Warp에서 lunarvim, lazyvim 또는 neovim에 직접 테마를 적용하여 사용하다 보면 아래와 같이 여백이…
Technical details about a maximum-severity Cisco IOS XE WLC arbitrary file upload flaw tracked as CVE-2025-20188 have been made publicly…
The quantum computing revolution is no longer a distant threat—it’s a reality that demands immediate action from cybersecurity leaders. Recent…