A severe security vulnerability in Synology’s DiskStation Manager (DSM) software has been identified. This vulnerability allows remote attackers to read…
Cybersecurity firm Volexity has tracked a series of highly targeted attacks by suspected Russian threat actors, identified as UTA0352 and…
The Trump administration’s plan to overhaul the State Department for the modern era could halt the U.S.’s recent progress on…
Phishing attacks remain a huge challenge for organizations in 2025. In fact, with attackers increasingly leveraging identity-based techniques over software…
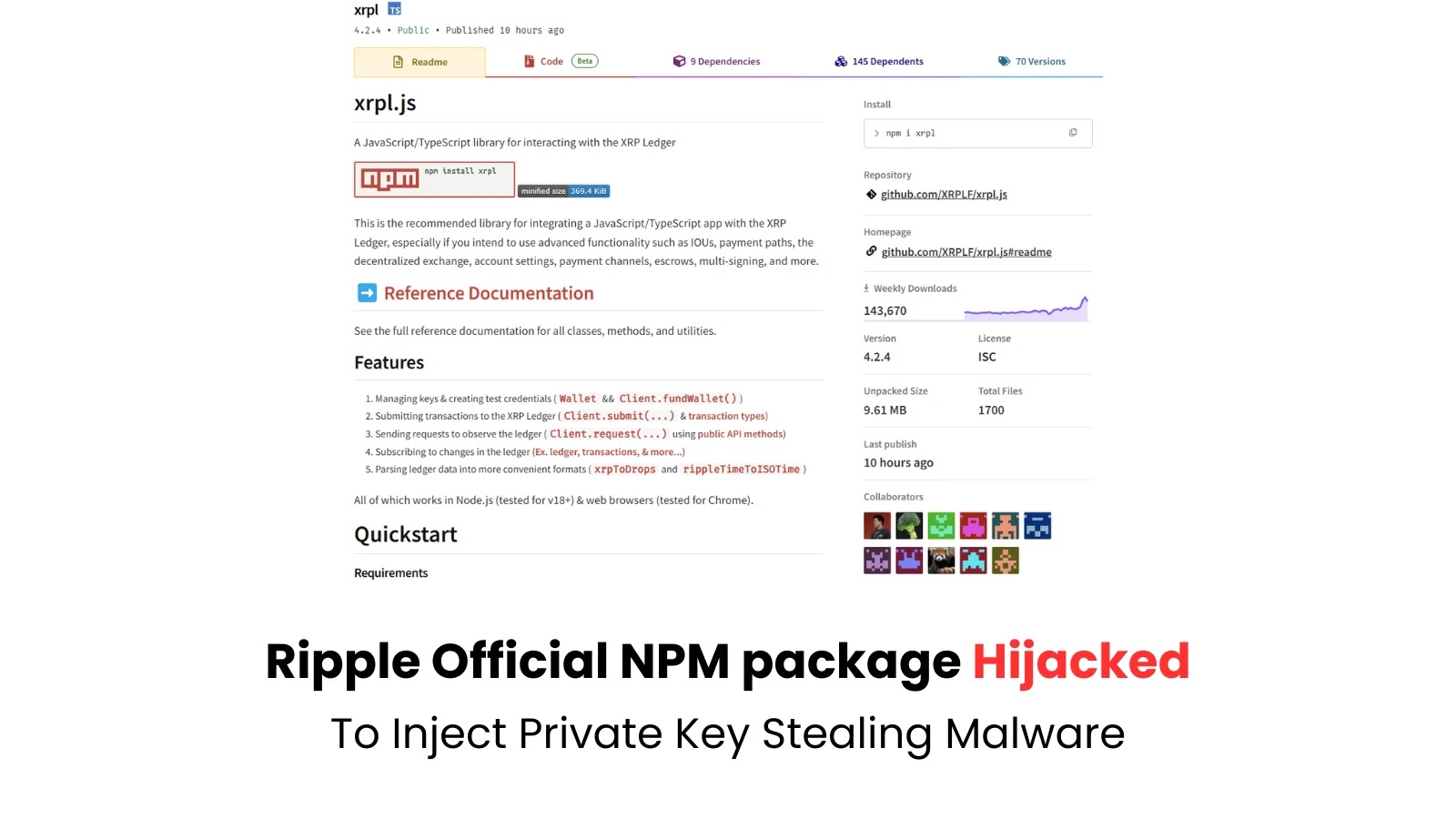
A significant supply chain attack targeting cryptocurrency users. The official XRPL (Ripple) NPM package, which serves as the JavaScript SDK…
Group-IB’s High-Tech Crime Trends Report 2025 reveals a sharp 22% surge in phishing websites, with over 80,000 detected in 2024….
Dive Brief: Despite fears, the recent waves of AI uptake have yet to require a cybersecurity overhaul, according to Verizon’s…
ASUS has released security updates to address CVE-2024-54085, a maximum severity flaw that could allow attackers to hijack and potentially…
The Evolving role of the Chief Information Security Officer (CISO) has transcended its roots in technical oversight to become a…
Unit 42’s 2025 Global Incident Response Report, ransomware actors are intensifying their cyberattacks, with 86% of incidents causing significant business…
If your iPhone feels cramped and storage alerts show up like it’s on a schedule, it’s probably time for a…
Blue Shield of California disclosed it suffered a data breach after exposing protected health information of 4.7 million members to…