A sophisticated backdoor targeting various large Russian organizations across government, finance, and industrial sectors has been uncovered during a cybersecurity…
CrowdStrike today announced the general availability of Falcon® Privileged Access, a breakthrough module in its Falcon® Identity Protection suite, aimed…
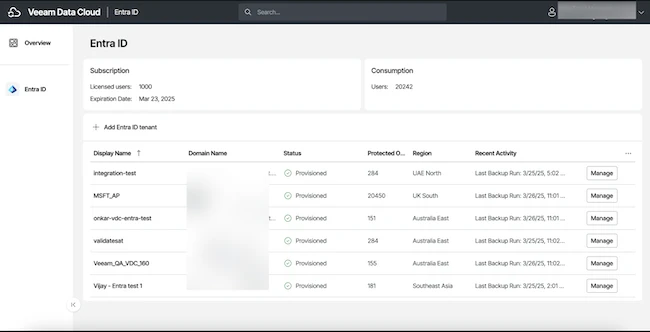
Veeam Software announced Veeam Data Cloud for Microsoft Entra ID. With Entra ID (formerly Azure AD) facing over 600 million…
Apr 23, 2025Ravie LakshmananBlockchain / Cryptocurrency The Ripple cryptocurrency npm JavaScript library named xrpl.js has been compromised by unknown threat…
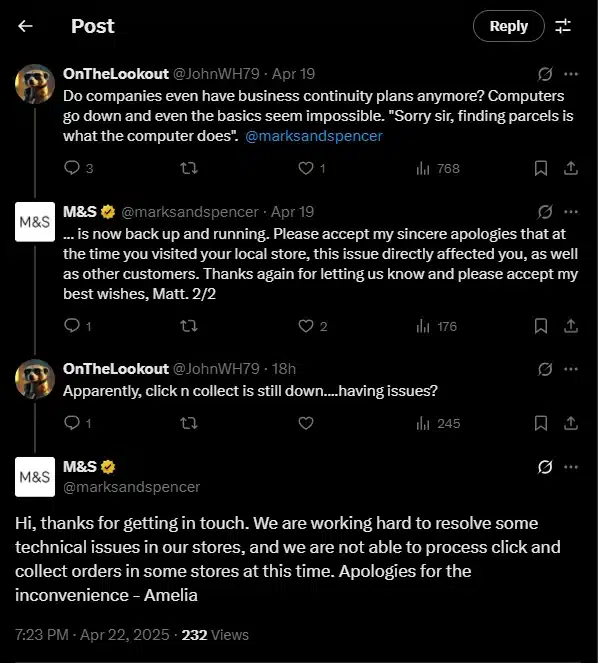
UK retail giant Marks & Spencer has confirmed it is managing a cybersecurity incident, following several days of service disruption…
I have a number of friends who actually post insightful ideas and comments on Facebook, and they do so semi-regularly….
Microsoft has fixed several known issues that caused Blue Screen of Death (BSOD) and installation issues on Windows Server 2025…
Leading British retailer Marks & Spencer Group plc (M&S) has confirmed it has been grappling with a cyberattack over the…
On April 21, 2025, British retail giant Mark and Spencer (M&S) confirmed that it was the victim of a cyberattack…
Application Security Analyst Greenway Health | India | Remote – View job details As an Application Security Analyst, you will…
I think a lot about creativity and how to maximize it, and one of my latest ideas has been to…
In this increasingly digital world, cybersecurity has become more than just an IT concern; it’s a critical aspect of every…