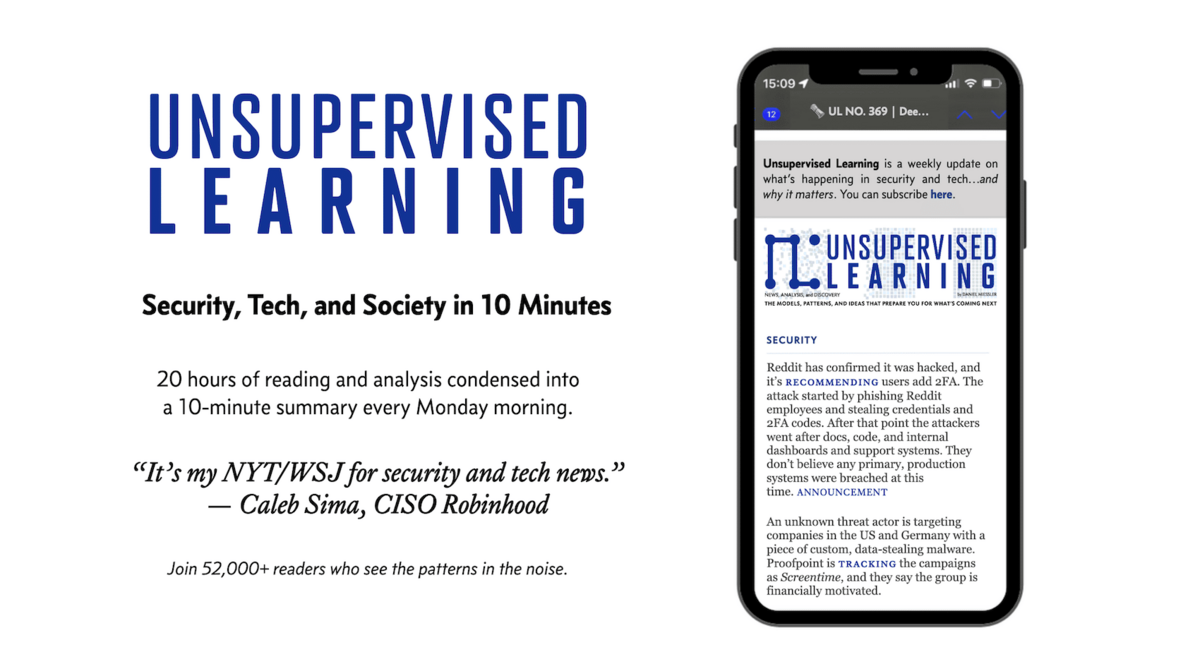
Apr 23, 2025Ravie LakshmananPrivacy / Artificial Intelligence Google on Tuesday revealed that it will no longer offer a standalone prompt…
A sophisticated attack technique dubbed “Cookie-Bite” enables cybercriminals to silently bypass multi-factor authentication (MFA) and maintain persistent access to cloud…
A recent security audit has uncovered critical vulnerabilities within Moodle, the widely used open-source learning management system (LMS). These vulnerabilities…
With billions of users, YouTube has become a tempting target for cybercriminals. They post malicious links in video descriptions and…
I don’t know a single truly creative mind who is a news junkie – not a writer, not a composer,…
Cybercriminals continued to shift to stealthier tactics, with lower-profile credential theft spiking, while ransomware attacks on enterprises declined, according to…
Google researchers have combined a number of reputation techniques to create a system that is 99 percent successful in detecting…
Cybercriminals and state-sponsored threat groups exploited vulnerabilities and initiated ransomware attacks with vigor last year, escalating the scope of their…
Because insurers are paid a fixed percentage of the claims they administer, they have no incentive to hold down costs….
A bird hit my windshield on the freeway, on the way home from work this morning. I pulled over on…
And when I say “this site”, I’m really saying “me”. Existentialism: How to create our own meaning and our own…
In a development that could transform vulnerability research, security researcher Matt Keeley demonstrated how artificial intelligence can now create working…