LockBit Ransomware Gang Becomes Victim of Data Breach The infamous LockBit ransomware group, known for its double extortion tactics and…
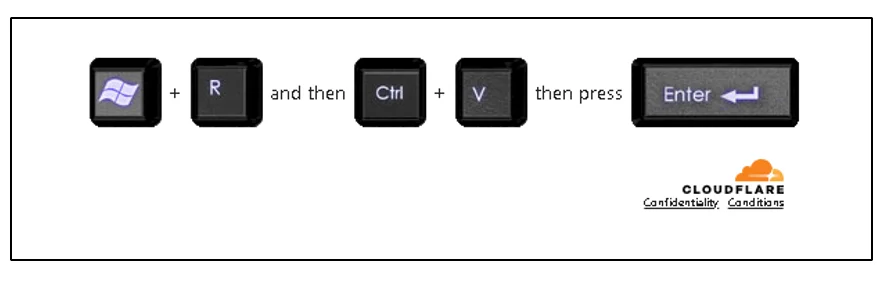
As new malware delivery campaigns using the ClickFix social engineering tactic are spotted nearly every month, it’s interesting to see…
May 08, 2025Ravie LakshmananNetwork Security / Vulnerability SonicWall has released patches to address three security flaws affecting SMA 100 Secure…
Several posts on DPRK IT workers infiltrating companies, Sentinel One on fighting off threat actors, Anthropic shares how attackers were…
Dive Brief: The FBI and the Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday warned of unsophisticated threat actors targeting…
Venture capital firm Insight Partners has confirmed that sensitive data for employees and limited partners was stolen in a January…
Cybersecurity specialists have devised an innovative approach to combat an emerging cybercrime called “PigButchering” on the Telegram platform. This form…
Hyper-converged infrastructure (HCI) pioneer and market leader Nutanix has added the ability to connect with external storage from Pure Storage…
Since the start of the year, the Russian state-backed ColdRiver hacking group has been using new LostKeys malware to steal…
A sophisticated spam campaign targeting Portuguese-speaking users in Brazil has been uncovered by Cisco Talos, active since at least January…
Cybercrime is rising globally, with 2025 costs estimated to dwarf amounts recorded in previous years. Highlighting the scale of the problem is…
For decades, passwords have been our default method for keeping online accounts safe. But in the age of artificial intelligence,…


![[tl;dr sec] #278 – North Korean IT Workers, How Sentinel One Defends Itself, How Threat Actors Use Claude [tl;dr sec] #278 - North Korean IT Workers, How Sentinel One Defends Itself, How Threat Actors Use Claude](https://image.cybernoz.com/wp-content/uploads/2025/05/tldr-sec-278-North-Korean-IT-Workers-How-Sentinel.png)







