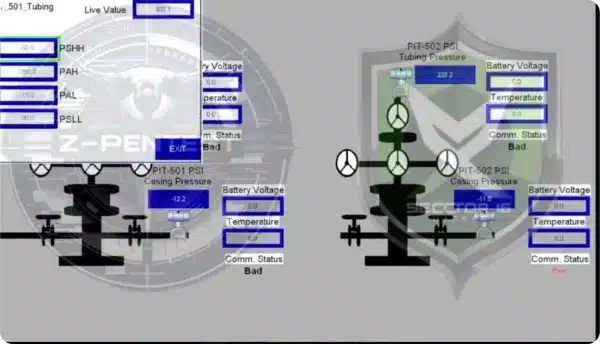
CISA warned critical infrastructure organizations of “unsophisticated” threat actors actively targeting the U.S. oil and natural gas sectors. While these attacks use very basic…
A startling discovery by Hunted Labs has brought to light a potential security risk lurking within the heart of the…
ClickFunnels is investigating a data breach after hackers leaked detailed business data, including emails, phone numbers, and company profiles. A…
A California court has ordered Israeli spyware merchant NSO Group to pay $167.25m in punitive damages, and $444,719 in compensatory…
Unsophisticated hackers are increasingly targeting industrial control systems (ICS) and supervisory control and data acquisition (SCADA) systems in the energy…
Passwords have long been the bedrock of online security, but the vulnerabilities are obvious, ranging from human error to phishing…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued a new alert warning critical infrastructure operators-particularly those in the oil…
The bank holiday weekend saw continuing disruption from a series of cyber attacks on the UK retail sector that have…
CrowdStrike said Wednesday that it would cut 500 jobs, or 5% of its global workforce, as part of a plan…
Passwords have long been the bedrock of online security, but the vulnerabilities are obvious, ranging from human error to phishing…
The Agenda ransomware group, also known as Qilin, has been reported to intensify its attacks in the first quarter of…
US jury orders NSO Group to pay $168M to WhatsApp and Meta over Pegasus spyware use in 2019 hack. Meta…