Canary Exploit tool allows to find servers affected by Apache Parquet flaw Pierluigi Paganini May 07, 2025 F5 Labs researchers…
A U.S. federal jury has ordered Israeli spyware vendor NSO Group to pay WhatsApp $167,254,000 in punitive damages and $444,719…
SpyCloud, the leading identity threat protection company, today released an analysis of nearly 6 million phished data records recaptured from…
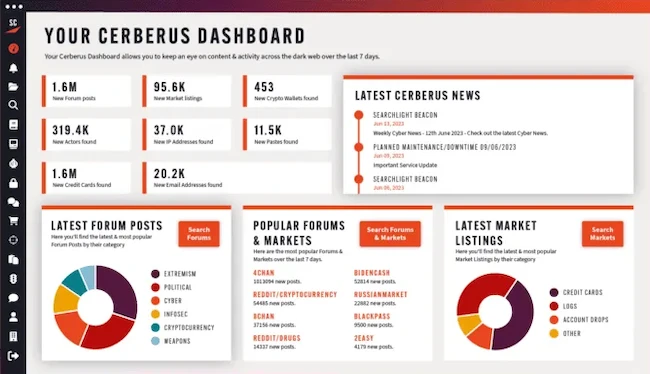
Searchlight Cyber has launched new AI capabilities within its dark web investigations platform, Cerberus. The new Cerberus AI Insights feature…
The FBI has issued a warning about an ongoing fraud scheme where criminal scammers are impersonating FBI Internet Crime Complaint…
May 07, 2025Ravie LakshmananDark Web / Cybercrime Europol has announced the takedown of distributed denial of service (DDoS)-for-hire services that…
Medical device company Masimo Corporation warns that a cyberattack is impacting production operations and causing delays in fulfilling customers’ orders….
The healthcare sector has emerged as a prime target for cyber attackers, driven by the increasing reliance on cloud applications…
Austin, USA / Texas, May 7th, 2025, CyberNewsWire SpyCloud, the leading identity threat protection company, today released an analysis of…
Austin, USA / Texas, May 7th, 2025, CyberNewsWire SpyCloud, the leading identity threat protection company, today released an analysis of…
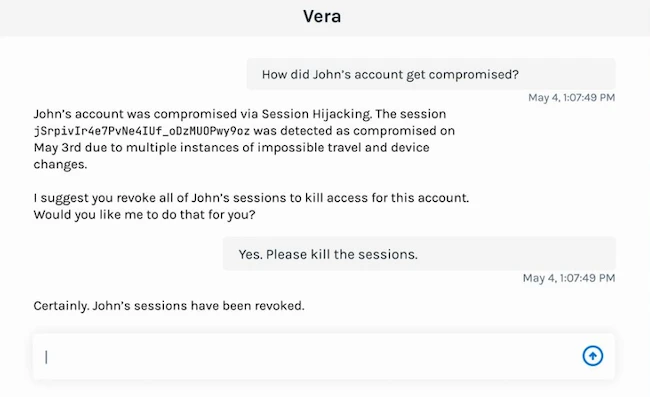
Verosint launched Vera, an agentic AI security analyst to transform how organizations detect, investigate, and respond to identity-based threats. Built…
Power supply problems remain the most common cause of “impactful” datacentre downtime incidents, but ransomware attacks are the leading cause…