U.S. CISA adds FreeType flaw to its Known Exploited Vulnerabilities catalog Pierluigi Paganini May 07, 2025 U.S. Cybersecurity and Infrastructure Security…
A newly disclosed security vulnerability in Elastic’s Kibana platform has put thousands of businesses at risk, with attackers able to…
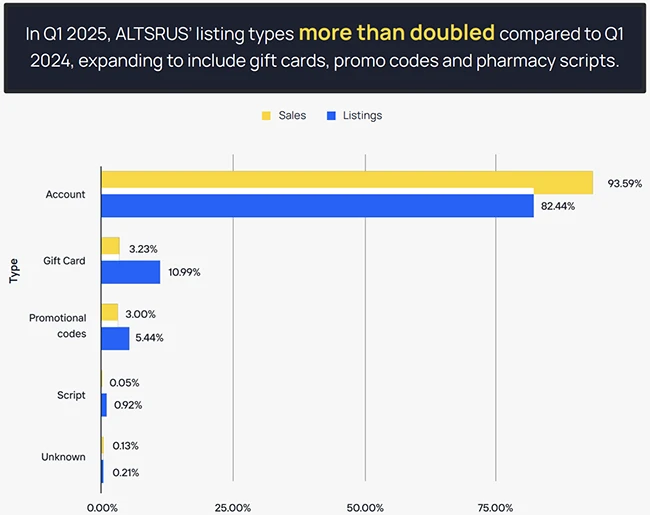
A new report from bot defense firm Kasada has exposed the growing threat of ALTSRUS, a fraud syndicate targeting some…
May 07, 2025Ravie LakshmananVulnerability / Spyware A federal jury on Tuesday decided that NSO Group must pay Meta-owned WhatsApp WhatsApp…
A former information technology manager has filed a whistleblower lawsuit alleging a major security breach at Deutsche Bank’s Manhattan headquarters,…
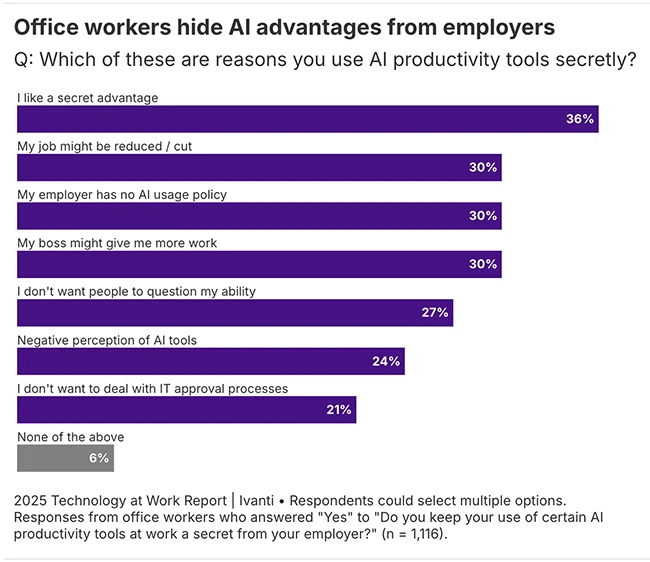
Employees are feeling heightened concerns around the use of technology to enhance productivity, as well as job dissatisfaction and a…
The California Privacy Protection Agency (CPPA) has announced that national clothing retailer Todd Snyder, Inc. must pay a $345,178 fine…
A federal jury in California has ordered Israeli spyware maker NSO Group to pay approximately $168 million in damages to…
Application security is changing fast. In this Help Net Security interview, Loris Gutic, Global CISO at Bright, talks about what…
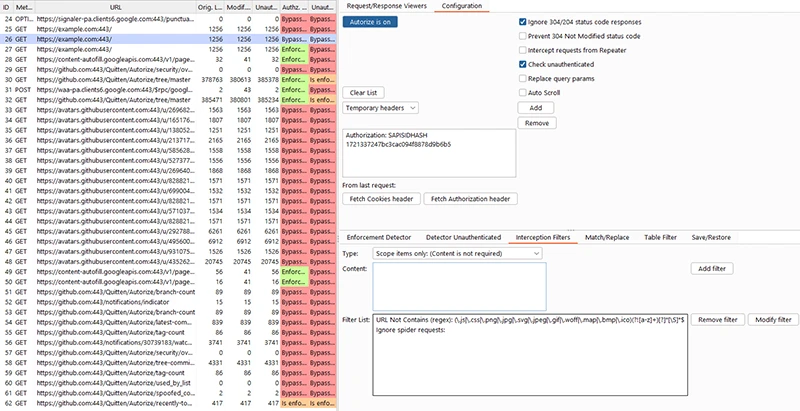
Autorize is an open-source Burp Suite extension that checks if users can access things they shouldn’t. It runs automatic tests…
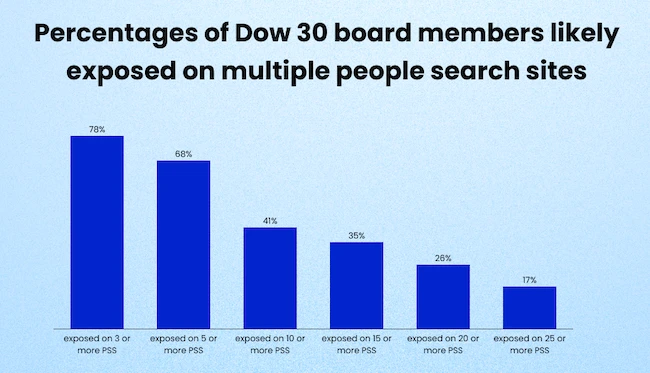
The personal information of 75% of corporate directors can be found on people search sites, according to Incogni. People search…
Football Australia is set to use AI camera technology and NBN connectivity at key venues to automatically capture and stream…