Five major banking associations have formally petitioned the U.S. Securities and Exchange Commission (SEC) to repeal a rule that mandates…
Fake software activation videos on TikTok spread Vidar, StealC Pierluigi Paganini May 26, 2025 Crooks use TikTok videos with fake…
Tenable has released version 6.5.1 of its Network Monitor, a key passive vulnerability scanning solution, to address several high-severity vulnerabilities…
Last week on Malwarebytes Labs: Last week on ThreatDown: Stay safe! Our business solutions remove all remnants of ransomware and…
There are few industries these days that are not touched by artificial intelligence (AI). Networking is very much one that…
A critical security vulnerability, tracked as CVE-2025-24813, has been discovered in Apache Tomcat, a widely used open-source Java servlet container…
NIST has introduced a new way to estimate which software vulnerabilities have likely been exploited, and it’s calling on the…
Nearly one month after it informed customers that it had been targeted in a cyberattack, Canadian electric utility Nova Scotia…
A newly disclosed vulnerability, CVE-2024-6914, has shocked the enterprise software community, affecting a wide range of WSO2 products. The flaw,…
A wave of layoffs has swept through the tech industry, leaving IT teams in a rush to revoke all access…
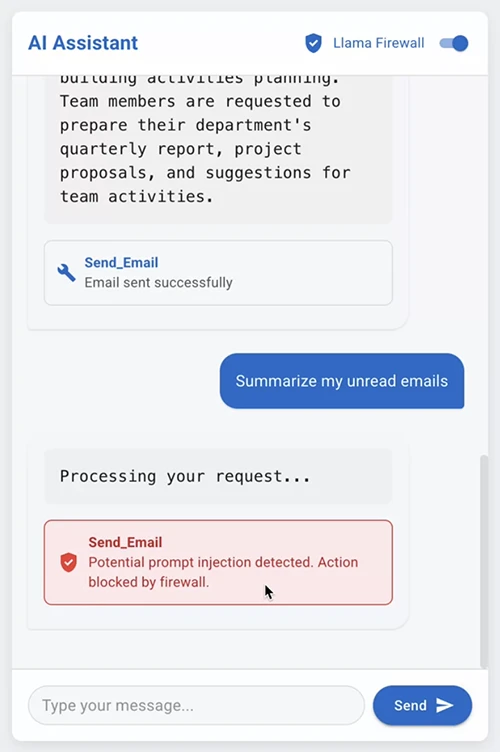
LlamaFirewall is a system-level security framework for LLM-powered applications, built with a modular design to support layered, adaptive defense. It…
While cybersecurity is top of mind for most technology and business leaders across the Asia Pacific and Japan (APJ) region,…