An employee at Elon Musk’s artificial intelligence company xAI leaked a private key on GitHub that for the past two months…
SAN FRANCISCO — The senior director for cyber at the White House’s National Security Council told an audience Thursday that…
Bitdefender researchers have uncovered a surge in subscription scams, both in scale and sophistication, spurred by a massive campaign involving…
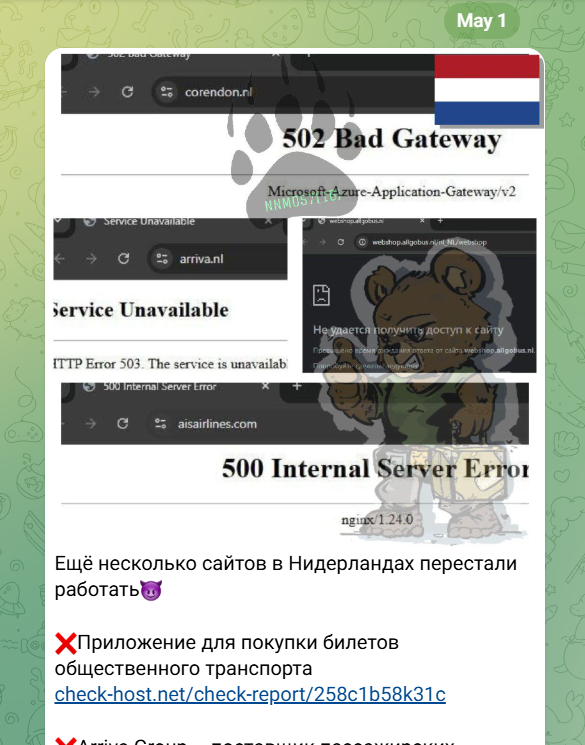
Pro-Russia hacktivist group NoName057(16) is targeting Dutch organizations Pierluigi Paganini May 01, 2025 Pro-Russia hacktivist group NoName057(16) is targeting Dutch…
Federal authorities extradited a Ukrainian citizen to the United States on Wednesday to face charges for participating in a series…
A California man who used the alias “NullBulge” has pleaded guilty to illegally accessing Disney’s internal Slack channels and stealing over…
In the digital age, preparing for cyber warfare is essential as organizations face unprecedented threats beyond traditional hacking and data…
Navigating healthcare cybersecurity is crucial in today’s hyper-connected environment, where it underpins both operational resilience and patient trust. The rapid…
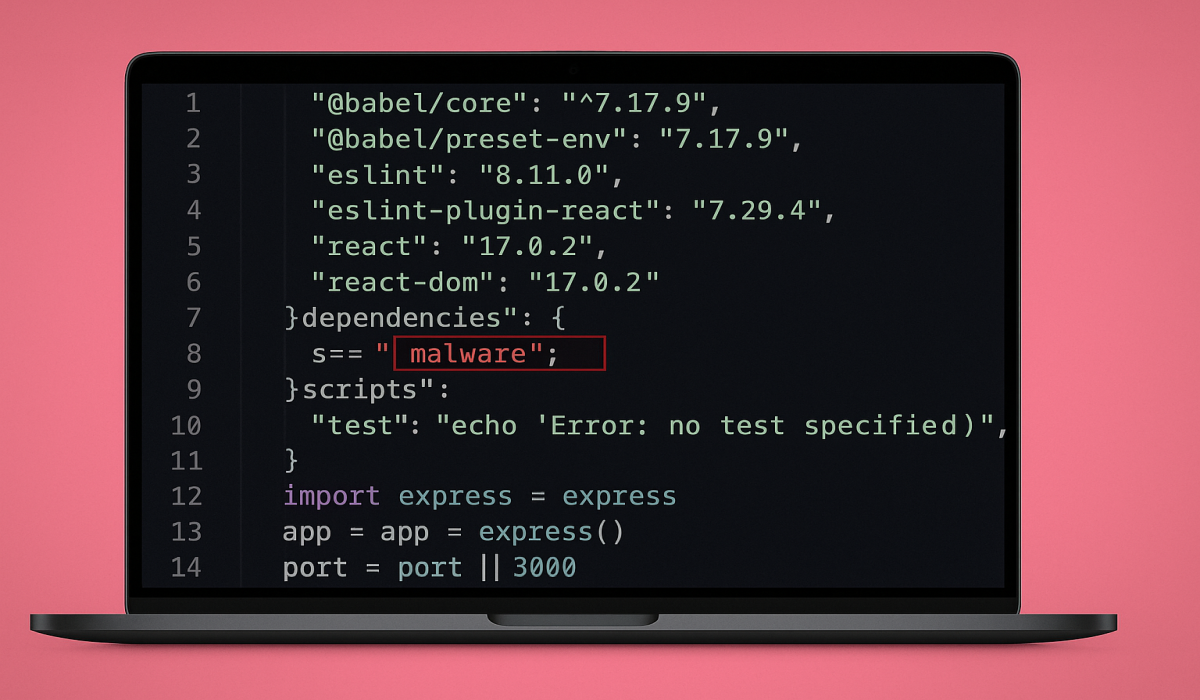
Sonatype discovered ‘crypto-encrypt-ts’, a malicious npm package impersonating the popular CryptoJS library to steal crypto and personal data. Over 1900…
Microsoft has forecast stronger-than-expected quarterly growth for its cloud-computing business Azure after blowout results in the latest quarter, calming investor…
AI as a primary focus Emphasis on attracting investment Trump visiting Gulf May 13-16 Artificial intelligence is anticipated to dominate…
In today’s digital-first business environment, protecting intellectual property is crucial, as IP remains one of an organization’s most valuable assets….