Virgin Australia is using the Kafka stream processing platform to power a growing range of customer experience features, from automated…
SAN FRANCISCO — Cryptography experts say the race to fend off future quantum-computer attacks has entered a decisive but measured…
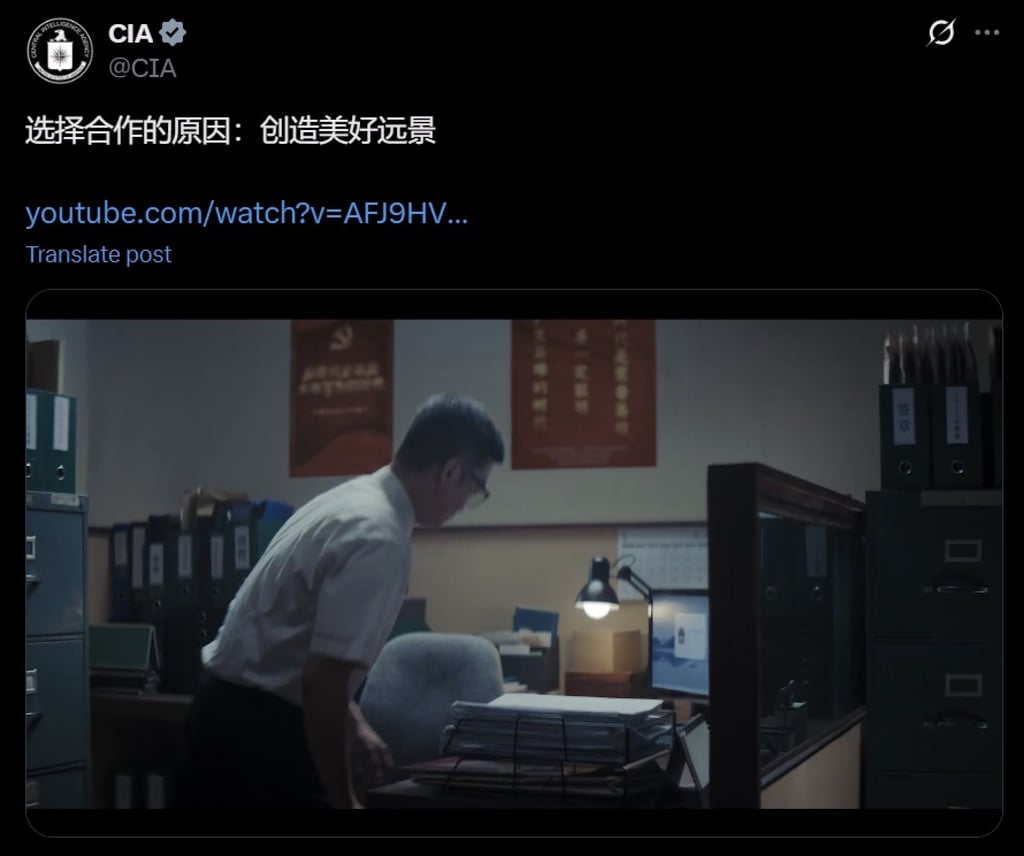
The CIA on Thursday rolled out two Chinese-language videos aimed at enticing officials in China to leak secrets to the…
A Ukrainian national has been extradited from Spain to the United States to face charges over allegedly conducting Nefilim ransomware…
Building a scalable cybersecurity framework is essential in today’s rapidly evolving digital landscape, enabling organizations to adapt to changing threats…
Sergey Nivens – stock.adobe.com By Mikey Hoare, crisis expert, Kekst CNC Published: 01 May 2025 The cyber attacks on M&S…
Russia-aligned hacktivists persistently target key public and private organizations in the Netherlands with distributed denial of service (DDoS) attacks, causing…
Quantum cybersecurity risks represent a paradigm shift in cybersecurity, demanding immediate attention from Chief Information Security Officers worldwide. While practical…
SEO: Cybercriminals are using the recent power outages in Spain and Portugal to launch phishing attacks disguised as TAP Air…
Application security in 2025 has become a defining concern for every Chief Information Security Officer (CISO) as organizations accelerate their…
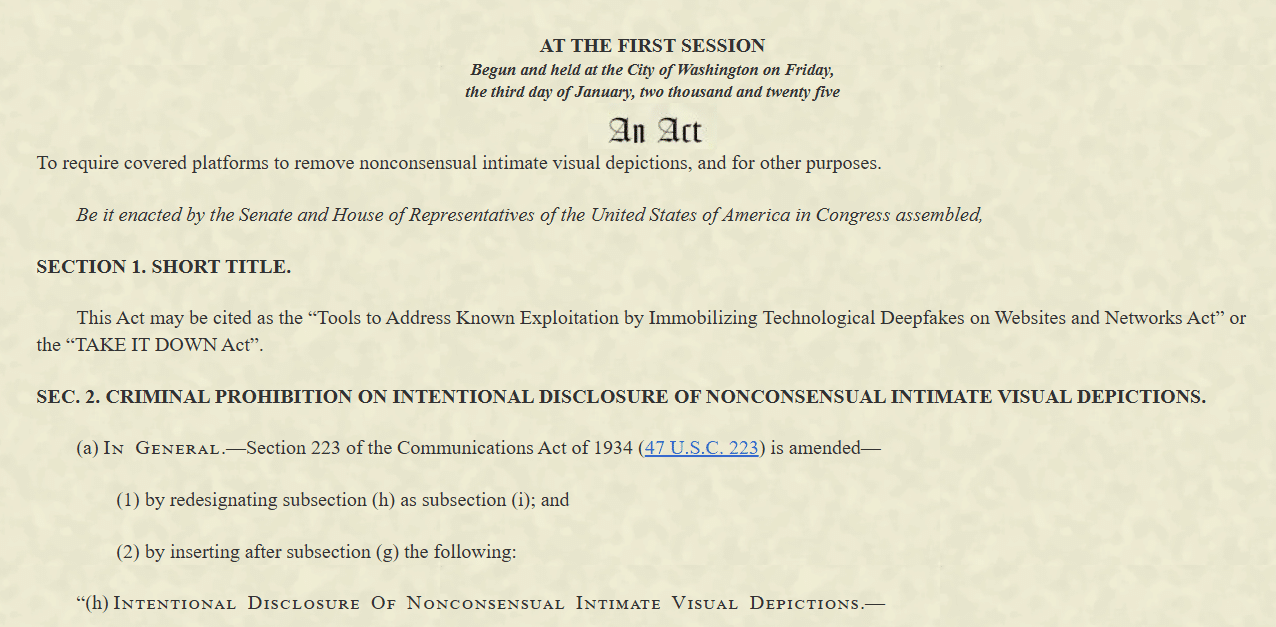
U.S. legislation to criminalize non-consensual intimate images, videos and deepfakes has passed Congress with the overwhelming support of both parties,…
FBI shared a list of phishing domains associated with the LabHost PhaaS platform Pierluigi Paganini May 01, 2025 The FBI…