Coca-Cola and its bottling partner, Coca-Cola Europacific Partners (CCEP), are facing separate cyberattack claims from two distinct threat groups. The…
Amazon is testing AI-powered short-form audio summaries on select product detail pages, the e-commerce giant said on Wednesday, as tech…
Datadog Security Research has uncovered a targeted malware campaign aimed at Solidity developers on Windows systems, using malicious Visual Studio…
Macquarie Banking and Financial Services (BFS) is starting to train and prepare its workforce now for a future that will…
Halo Security, a leading provider of attack surface management and penetration testing services, today announced it has successfully achieved SOC 2 Type 1…
The Australian Energy Market Commission is considering new rules to manage an expected influx of high-capacity data centres in coming…
The U.S. government has indicted Russian national Rustam Rafailevich Gallyamov, the leader of the Qakbot botnet malware operation that compromised…
The hacker ecosystem in Russia, more than perhaps anywhere else in the world, has long blurred the lines between cybercrime,…
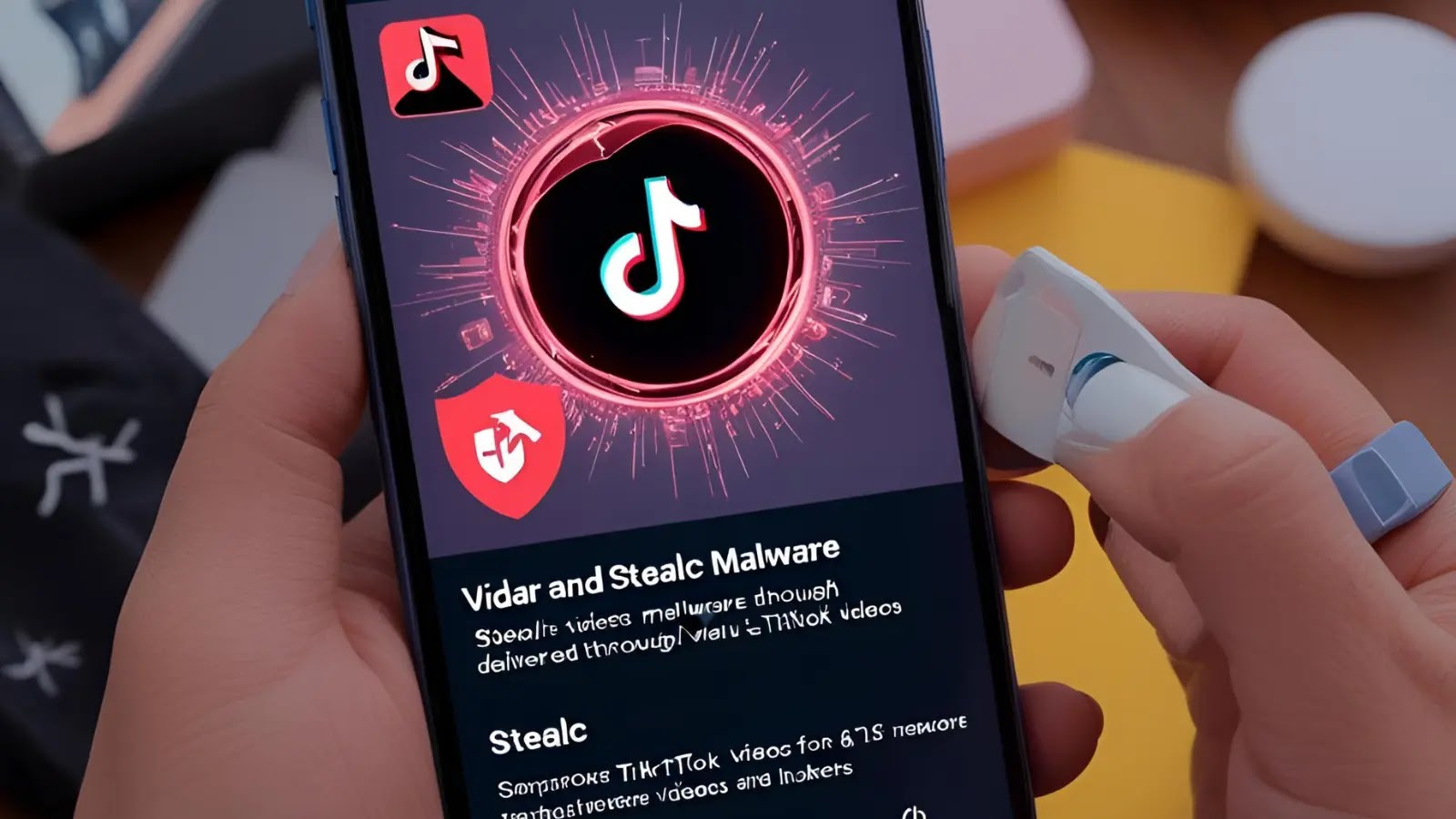
A sophisticated social engineering campaign that leverages the viral power of TikTok to distribute dangerous information-stealing malware, specifically Vidar and…
Federal Communications Commission Chair Brendan Carr told Congress the agency is looking to expand the use of call authentication protocols…
If you 3D print a frame of a Glock-style pistol, then you can buy the rest of the parts off…
A critical security vulnerability has been discovered in Netwrix Password Secure, a widely used enterprise password management solution, potentially allowing…