Two of the internet’s most critical infrastructure providers experienced significant service outages yesterday, disrupting millions of users worldwide as both…
Matt Salier has resigned as chief executive officer of the Australian Cyber Collaboration Centre, effective immediately. Salier calls it a…
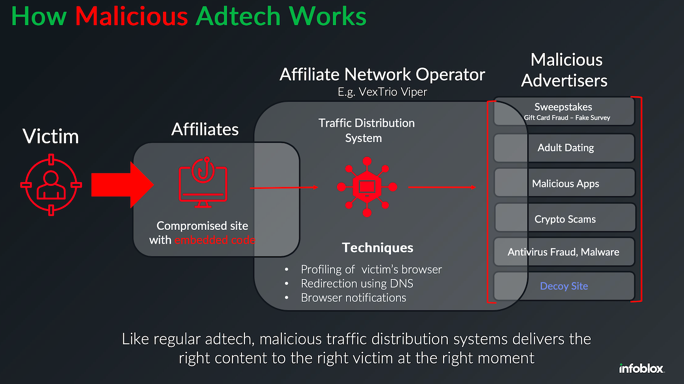
Late last year, security researchers made a startling discovery: Kremlin-backed disinformation campaigns were bypassing moderation on social media platforms by…
Huawei Technologies is capable of producing no more than 200,000 advanced artificial intelligence chips in 2025, a top US exports…
GO Markets has filed suit against a former chief information officer, alleging he arranged “secret commissions” from at least one…
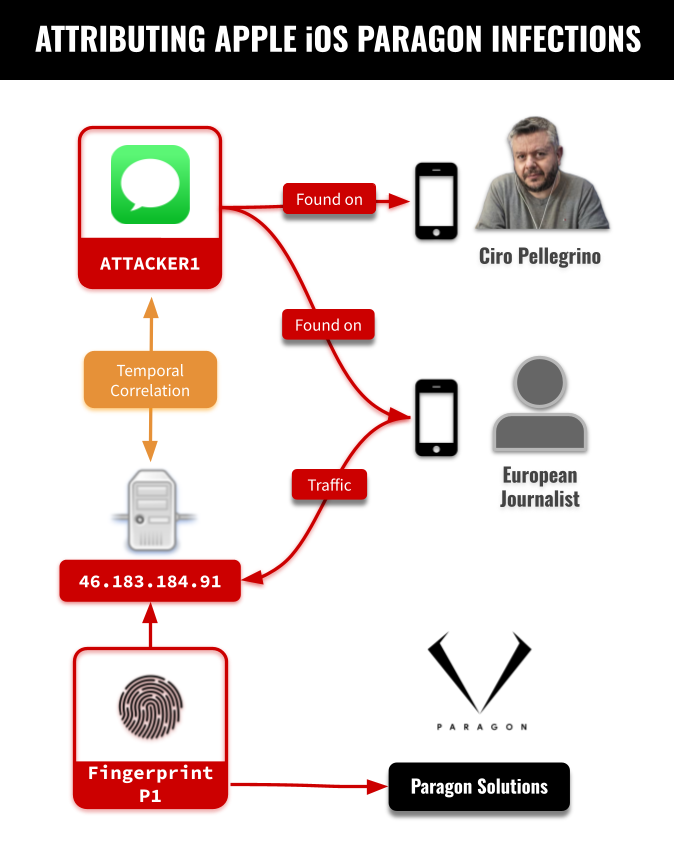
Paragon Graphite Spyware used a zero-day exploit to hack at least two journalists’ iPhones Pierluigi Paganini June 12, 2025 Security…
Remote Access Trojans (RATs) like Quasar have been a persistent threat for years, enabling attackers to control infected systems remotely. Recent…
Multiple platforms including music streaming service Spotify and instant messaging platform Discord were down for tens of thousands of users…
Microsoft has resolved a critical bug in Windows Server 2025 that caused Active Directory Domain Controllers to improperly manage network…
A new, highly sophisticated cyberattack campaign is targeting users seeking to download the popular language model DeepSeek-R1, exploiting global interest…
Trend Micro has released security updates to address multiple critical-severity remote code execution and authentication bypass vulnerabilities that impact its…
A sophisticated cyber threat campaign leveraging malicious unsubscribe links has emerged as a significant security concern, targeting unsuspecting email users…