If you insist on using biometric unlocking methods to have faster access to your devices, keep in mind that some…
Security researchers have uncovered a sophisticated malware campaign exploiting a little-known flaw in Discord’s invitation system, enabling cybercriminals to hijack…
Recorded Future said on Thursday that it had linked Intellexa infrastructure to new locations, the latest indication that the Predator…
Google Cloud and Cloudflare are investigating ongoing outages impacting access to sites and various services across multiple regions. Cloudflare first…
A critical command injection vulnerability in Palo Alto Networks PAN-OS operating system enables authenticated administrative users to escalate privileges and…
A critical vulnerability in OpenPGP.js, a widely used JavaScript library for encrypted messaging and digital signatures, has been patched after…
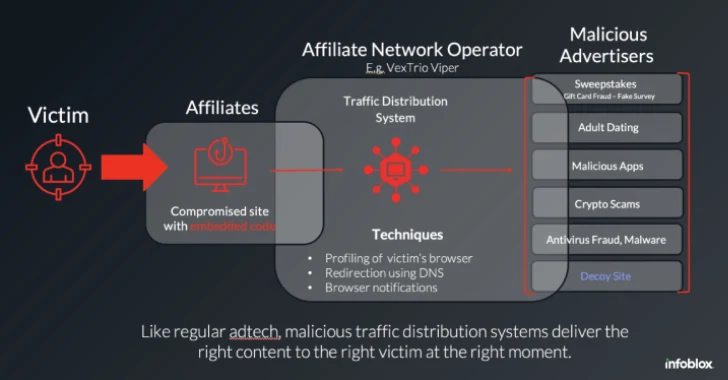
Jun 12, 2025Ravie LakshmananThreat Intelligence / Malware The threat actors behind the VexTrio Viper Traffic Distribution Service (TDS) have been…
A critical vulnerability in the widely-used OpenPGP.js library has been discovered that allows attackers to forge digital signatures and deceive…
Alerts about operations are disseminated through direct messages, WhatsApp, or posts on each page’s feed. In turn, it is possible…
A newly discovered remote access trojan (RAT) named CyberEye is making waves in the cybersecurity community for its sophisticated capabilities and its…
Forensic investigation has confirmed the use of Paragon’s Graphite spyware platform in zero-click attacks that targeted Apple iOS devices of…
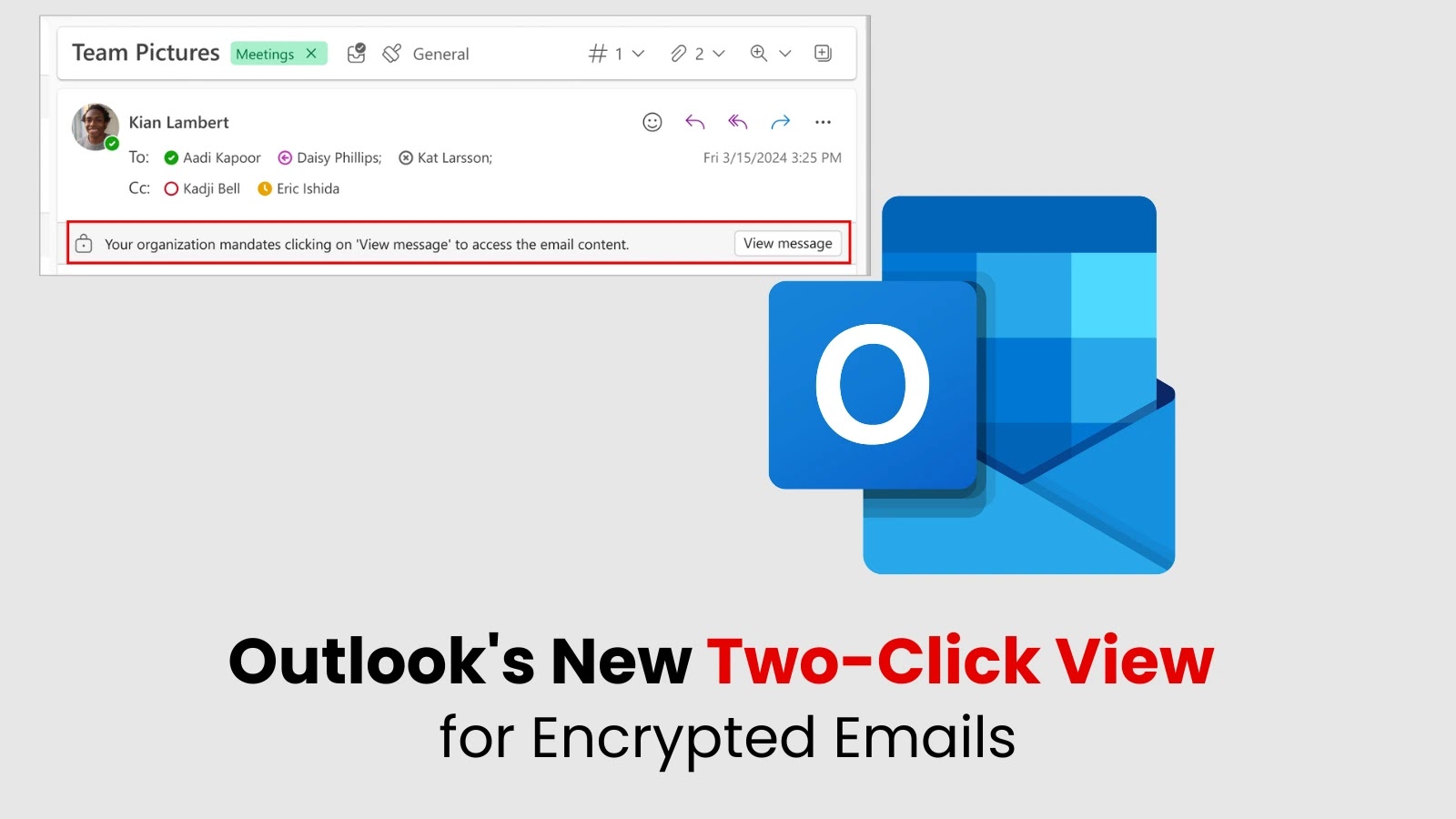
Microsoft is set to launch a significant security enhancement for Outlook users across multiple platforms. Starting April 2025, the company…