Jun 12, 2025Ravie LakshmananEnterprise Security / Active Directory Cybersecurity researchers have uncovered a new account takeover (ATO) campaign that leverages…
98% of CISOs face challenges when using threat intelligence, according to Trellix. The biggest problems are keeping up with changing…
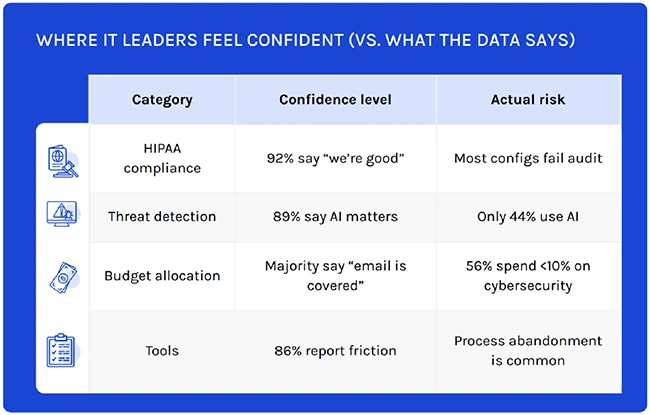
92% of healthcare IT leaders say they’re confident in their ability to prevent email-based data breaches, but according to Paubox,…
A critical zero-click vulnerability in Microsoft 365 Copilot, dubbed “EchoLeak,” enables attackers to automatically exfiltrate sensitive organizational data without requiring…
Nearly half of of mobile users encounter mobile scams daily, with people in the US and UK more likely to…
The Northern Beaches Women’s Shelter (NBWS) is seeking assistance on behalf of vulnerable women experiencing technology-enabled and cyber abuse, a…
Webjet Group has appointed Oonagh Flanagan as its first chief marketing officer in Australia as it enters a “new era…
Digital rights groups are urging Senate leaders not to move forward with a bill that would impose new regulations on…
Acronis has named Terry Christie as General Manager for Australia and New Zealand, signalling the company’s ongoing investment in the…
Tech company Cisco has released improvements to help enterprises improve security for the AI era, fusing security capabilities deeper into…
ChatGPT o3 API is now cheaper for developers, and there’s no visible impact on performance. On Wednesday, OpenAI announced it’s…
by Gary Miliefsky, Publisher, Cyber Defense Magazine In the shadowy corners of the internet, war is already underway. It doesn’t…