The NHS has emerged as a big winner from the government’s Spending Review through to 2027 with approximately £10bn allocated…
Listen to the article 2 min This audio is auto-generated. Please let us know if you have feedback. An international…
Two House Democratic leaders are asking a government watchdog to dig into two federally-funded initiatives to catalog software flaws and…
Secure code review represents a critical security practice that systematically examines software source code to identify and remediate security vulnerabilities…
Microsoft confirmed a critical security vulnerability (CVE-2025-47176) in Microsoft Office Outlook, enabling attackers to execute arbitrary code. Despite the “Remote…
Dive Brief: United Natural Foods, Inc. is currently serving customers on only a “limited basis” as it works to recover…
Microsoft confirmed on Tuesday that it’s pushing a revised security update targeting some Windows 11 24H2 systems incompatible with the…
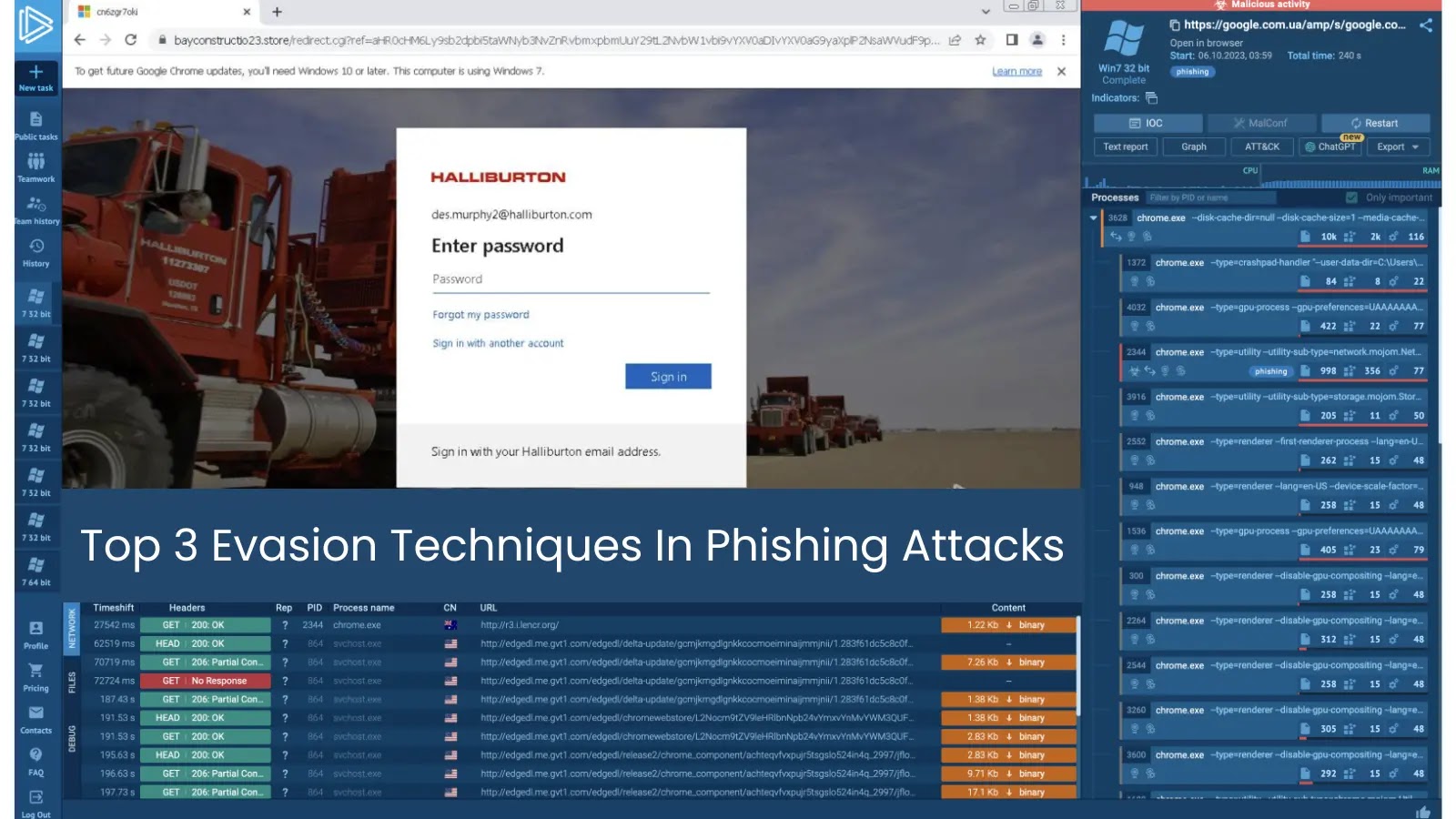
Phishing attacks aren’t what they used to be. Hackers no longer rely on crude misspellings or sketchy email addresses. Instead,…
Microsoft’s Patch Tuesday updates for June 2025 include fixes for an actively exploited zero-day vulnerability and nine additional flaws at…
A recently fixed critical vulnerability in Microsoft’s Copilot AI tool could have let a remote attacker steal sensitive data from…
An APT hacking group known as ‘Stealth Falcon’ exploited a Windows WebDav RCE vulnerability in zero-day attacks since March 2025 against…
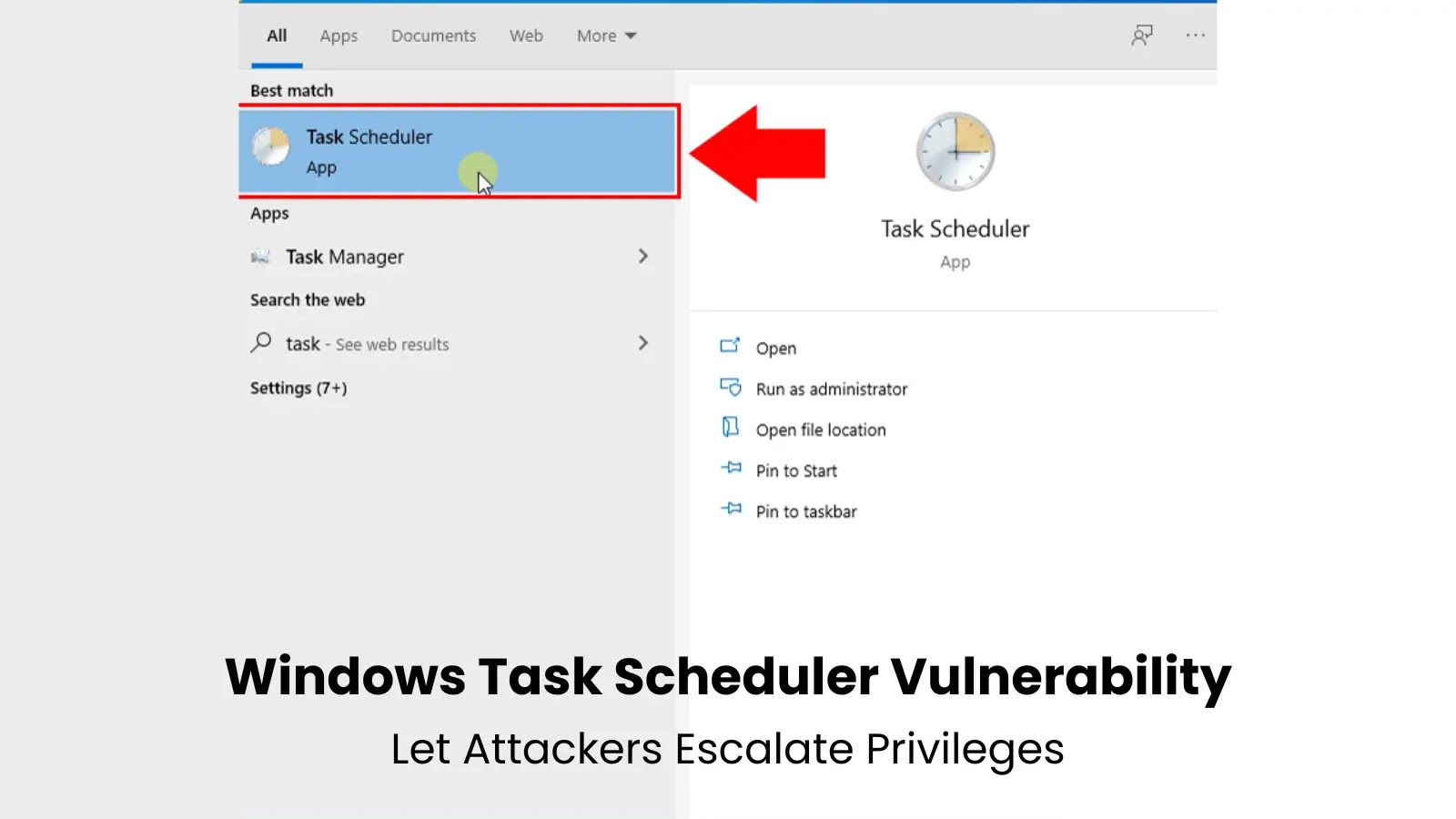
A significant security vulnerability in Windows Task Scheduler could allow attackers to escalate their privileges to SYSTEM level access without…