Jun 11, 2025Ravie LakshmananNetwork Security / Threat Intelligence Threat intelligence firm GreyNoise has warned of a “coordinated brute-force activity” targeting…
A coordinated campaign of brute-force attacks using hundreds of unique IP addresses targets Apache Tomcat Manager interfaces exposed online. Tomcat…
Microsoft addressed a critical security flaw (CVE-2025-32713) in the Windows Common Log File System (CLFS) driver during its June 2025…
Connectwise customers who use the company’s ScreenConnect, Automate, and ConnectWise RMM solutions are urged to update all agents and/or validate…
West Brom Building Society is embarking on a three-stage project to build the digital capabilities its customers want. The organisation,…
Listen to the article 8 min This audio is auto-generated. Please let us know if you have feedback. NATIONAL HARBOR,…
An international law enforcement action codenamed “Operation Secure” targeted infostealer malware infrastructure in a massive crackdown across 26 countries, resulting…
A critical elevation of privilege vulnerability has been identified in the Windows Task Scheduler service, tracked as CVE-2025-33067. Officially published…
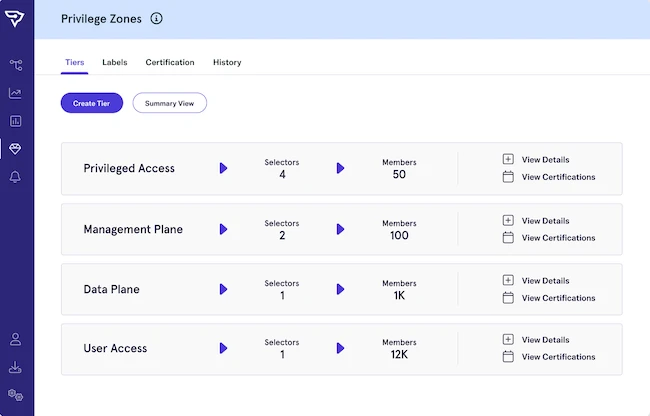
SpecterOps introduced Privilege Zones, a new addition to its flagship BloodHound Enterprise platform. Privilege Zones enable teams to define custom…
The government is using national security as a “smokescreen” to refuse to disclose how many technical capability notices (TCNs) it…
Microsoft has resolved a known issue that caused some Windows Server 2025 domain controllers to become unreachable after a restart…
Ransomware attacks are no longer just a cybersecurity concern – they are a direct threat to national security. A recent study found…