For June 2025 Patch Tuesday, Microsoft has fixed 66 new CVEs, including a zero-day exploited in the wild (CVE-2025-33053). Also,…
In today’s security landscape, budgets are tight, attack surfaces are sprawling, and new threats emerge daily. Maintaining a strong security…
Chancellor Rachel Reeves has committed up to £750m in funding to create the UK’s most powerful supercomputer at the University…
Insider threats represent one of the most challenging cybersecurity risks facing modern organizations, with research indicating that insider data leaks…
Apache CloudStack, a leading open-source cloud management platform, has announced the immediate availability of new Long-Term Support (LTS) releases—version 4.19.3.0…
Jun 11, 2025Ravie LakshmananIoT Security / Vulnerability Two security vulnerabilities have been disclosed in SinoTrack GPS devices that could be…
Microsoft has announced the introduction of two powerful new data tables to its Defender XDR advanced hunting capabilities, marking a…
Microsoft is set to revolutionize enterprise security monitoring with comprehensive audit logging capabilities for screen sharing and control features in…
HPE Aruba Networking has issued a critical security advisory regarding a high-severity vulnerability in its Private 5G Core Platform. Tracked…
The UK’s Cyber Security and Resilience (CSR) Bill represents a golden opportunity to enhance Britain’s national cyber security posture but…
Microsoft has released patches to fix 67 security flaws, including one zero-day bug in Web Distributed Authoring and Versioning (WEBDAV)…
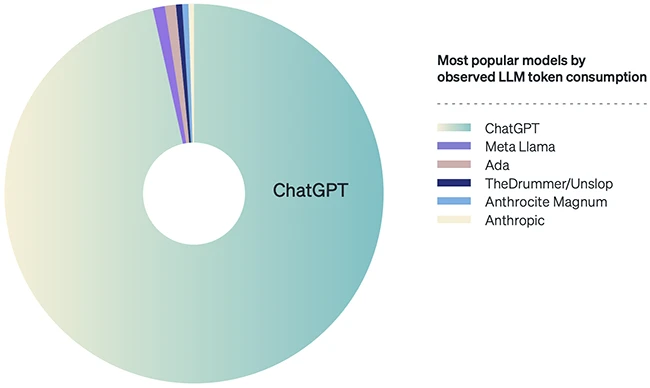
ChatGPT remains the most widely used LLM among New Relic customers, making up over 86% of all tokens processed. Developers…