The “cyber incident” that British multinational retailer Marks & Spencer has been struggling with for over a week is a…
AI search service Perplexity AI doesn’t just want you using its app—it wants to take over your web browsing experience…
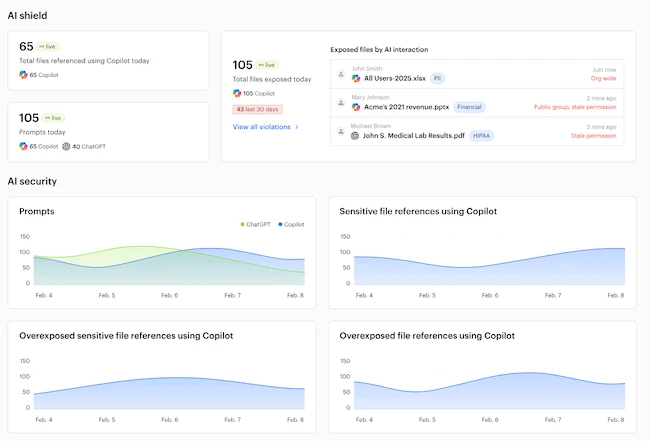
Find out how Reco keeps Microsoft 365 Copilot safe by spotting risky prompts, protecting data, managing user access, and identifying…
VeriSource data breach impacted 4M individuals Pierluigi Paganini April 29, 2025 VeriSource breach exposed data of 4M people in Feb…
Listen to the article 3 min This audio is auto-generated. Please let us know if you have feedback. Dive Brief:…
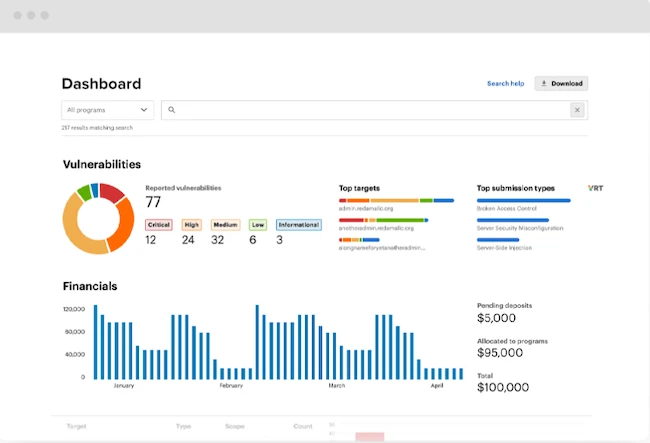
Bugcrowd’s new service connects customers with a global network of vetted ethical hackers for a variety of red team engagements—fully…
Your iPhone isn’t necessarily as invulnerable to security threats as you may think. Here are the key dangers to watch…
Microsoft announced that hotpatching support for Windows Server 2025 will become generally available as a subscription service starting July 1,…
Varonis announced always-on AI risk defense that continuously identifies data exposure in real time, flags violations, and automatically fixes issues…
Veeam is all set to fully launch version 13 of its Veeam Data Platform (VDP) – the platform upon which…
Law enforcement agencies from the UK and the Netherlands have dismantled the notorious JokerOTP cybercrime platform, which is allegedly linked…
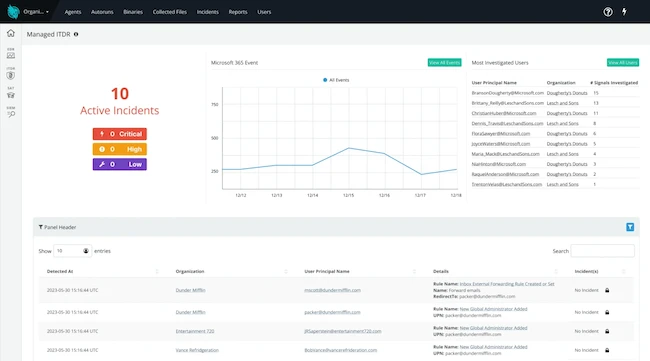
Huntress has unveiled its newly enhanced Managed Identity Threat Detection and Response (ITDR) solution, purpose-built to wreck hacker identity tradecraft,…