A discovery by Socket’s Threat Research Team has unveiled a malicious Python package named imad213, masquerading as an Instagram growth…
Cybersecurity experts at Akamai have uncovered a new threat: two separate botnets are actively exploiting a critical flaw in Wazuh…
Ingenia, an ASX-listed operator of holiday and residential communities, has spent the past two years optimising its HR and payroll…
Texas Department of Transportation (TxDOT) data breach exposes 300,000 crash reports Pierluigi Paganini June 10, 2025 Hackers breached Texas DOT…
AI is everywhere. Copilots help employees boost productivity, and agents provide front-line customer support. LLMs enable businesses to extract deep…
Microsoft has rolled out the June 2025 Patch Tuesday update for Windows 11, version 24H2, with the release of KB5060842…
A recent report by Kaspersky ICS CERT, released on June 10, 2025, sheds light on the persistent and evolving cyberthreats…
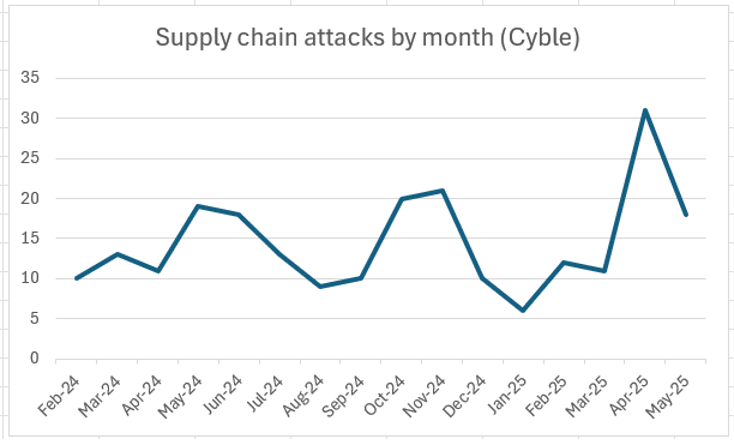
IT and software supply chain attacks have surged in recent months, as threat actors have gotten better at exploiting supply…
United Natural Foods’ operations remain significantly impacted by a cyberattack that prompted the company to completely shut its network down…
Security researchers have disclosed a new Secure Boot bypass tracked as CVE-2025-3052 that can be used to turn off security…
India’s Central Bureau of Investigation successfully dismantled a sophisticated transnational cybercriminal network that impersonated Microsoft technical support services, targeting vulnerable…
A critical zero-day vulnerability in Microsoft Windows, designated CVE-2025-33053, has been actively exploited by the advanced persistent threat (APT) group…