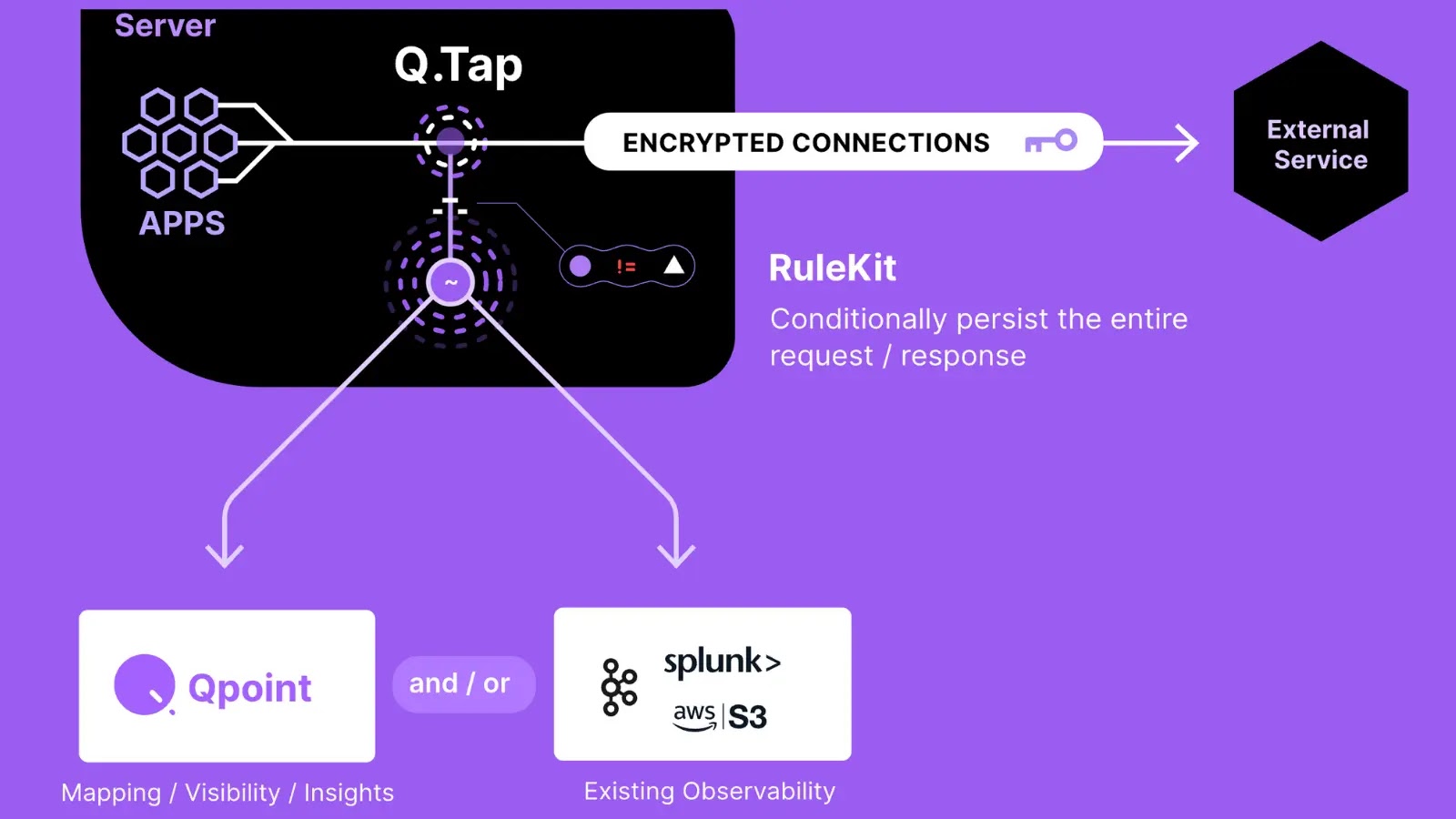
Qpoint has released Qtap, an open-source eBPF agent for monitoring network traffic in Linux systems. It hooks into TLS/SSL functions…
A critical security vulnerability has been identified in ISPConfig version 3.2.12p1, a widely used open-source web hosting control panel. The…
The UK’s financial services regulator has teamed up with Nvidia to provide an environment to enable finance firms to test…
Marks & Spencer on Tuesday said it has resumed limited online-ordering capabilities after an April cyberattack that led to major…
Ivanti has released security updates to fix three high-severity hardcoded key vulnerabilities in the company’s Workspace Control (IWC) solution. IWC…
Security analysts at CyberProof’s Security Operations Center (SOC) have identified a sharp rise in phishing campaigns leveraging Microsoft SharePoint to…
Phishing attackers abuse TLDs like .li, .es, and .dev to hide redirects, steal credentials, and bypass detection. See top domains…
Cybersecurity researchers have shed light on a previously undocumented Rust-based information stealer called Myth Stealer that’s being propagated via fraudulent…
SCI Semiconductors, a Cambridge-based tech company working on Capability Hardware Enhanced Risc Instructions (Cheri) systems to manage cyber defences, is…
Listen to the article 4 min This audio is auto-generated. Please let us know if you have feedback. NATIONAL HARBOR,…
Heroku is suffering a widespread outage that has lasted over six hours, preventing developers from logging into the platform and…
Ivanti has released a critical security update for its Workspace Control software, patching three high-severity vulnerabilities that could allow attackers…