A severe security vulnerability has been identified in ManageEngine Exchange Reporter Plus that could allow attackers to execute arbitrary commands…
Sensata Technologies, Inc., a major technology company based in Attleboro, Massachusetts, has disclosed a significant cybersecurity incident that compromised personal…
Jun 10, 2025Ravie LakshmananCryptocurrency / Malware The threat actor known as Rare Werewolf (formerly Rare Wolf) has been linked to…
SAP released its monthly Security Patch Day update addressing 14 critical vulnerabilities across multiple enterprise products. The comprehensive security update…
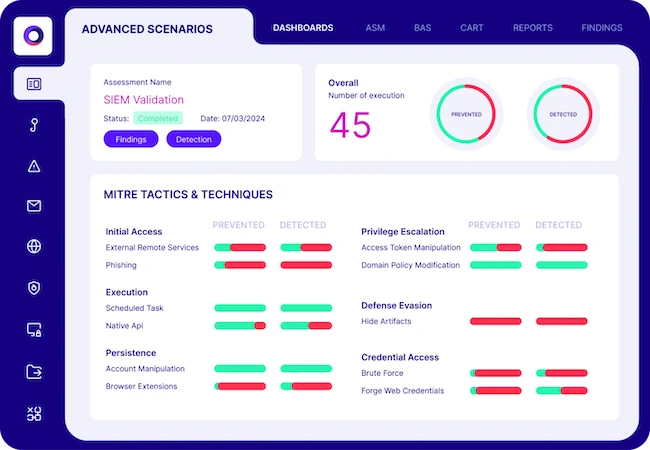
Cymulate releaseed AI-powered detection engineering assistant for security information and event management (SIEM) rule threat coverage validation. Now, the Cymulate…
Microsoft has until 25 July 2025 to respond to a £2bn legal claim, filed on behalf of thousands of UK…
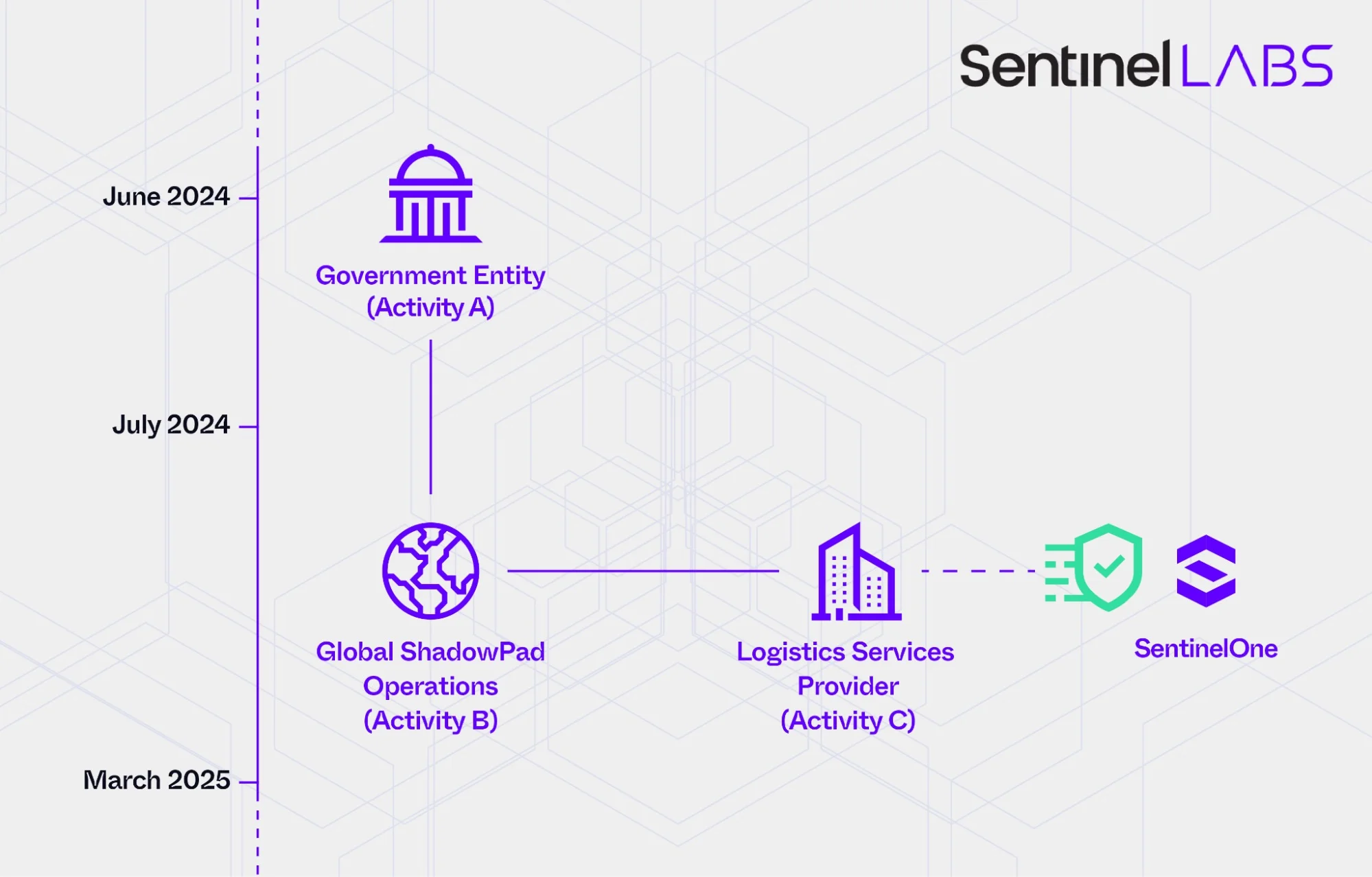
China-linked threat actor targeted +70 orgs worldwide, SentinelOne warns Pierluigi Paganini June 10, 2025 China-linked threat actor targeted over 70…
Automation tester (Infosec) – Vulnerability management WTW | India | On-site – View job details As an Automation tester (Infosec)…
No modern IT expert would recommend forgoing antivirus, endpoint detection and response or backup. And yet, many Australian organisations find…
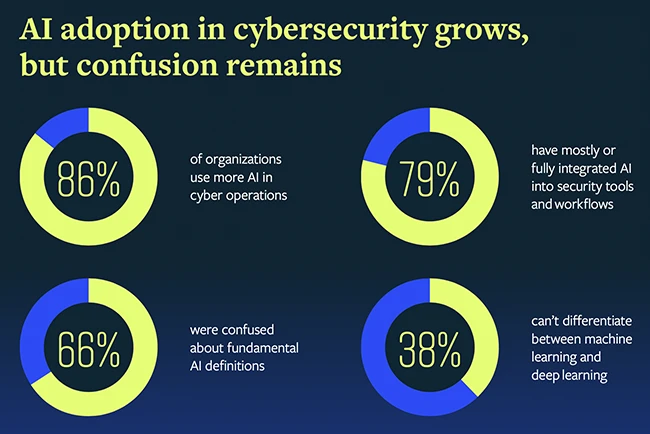
Security teams are leaning hard into AI, and fast. A recent survey of 500 senior cybersecurity pros at big U.S….
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added two critical security flaws impacting Erlang/Open Telecom Platform (OTP)…
As Australian organisations accelerate digital transformation and AI reshapes the fabric of enterprise operations, Australia faces a pivotal moment in…