We recently released The Rise of Agentic AI, our API ThreatStats report for Q1 2025, finding that evolving API threats are…
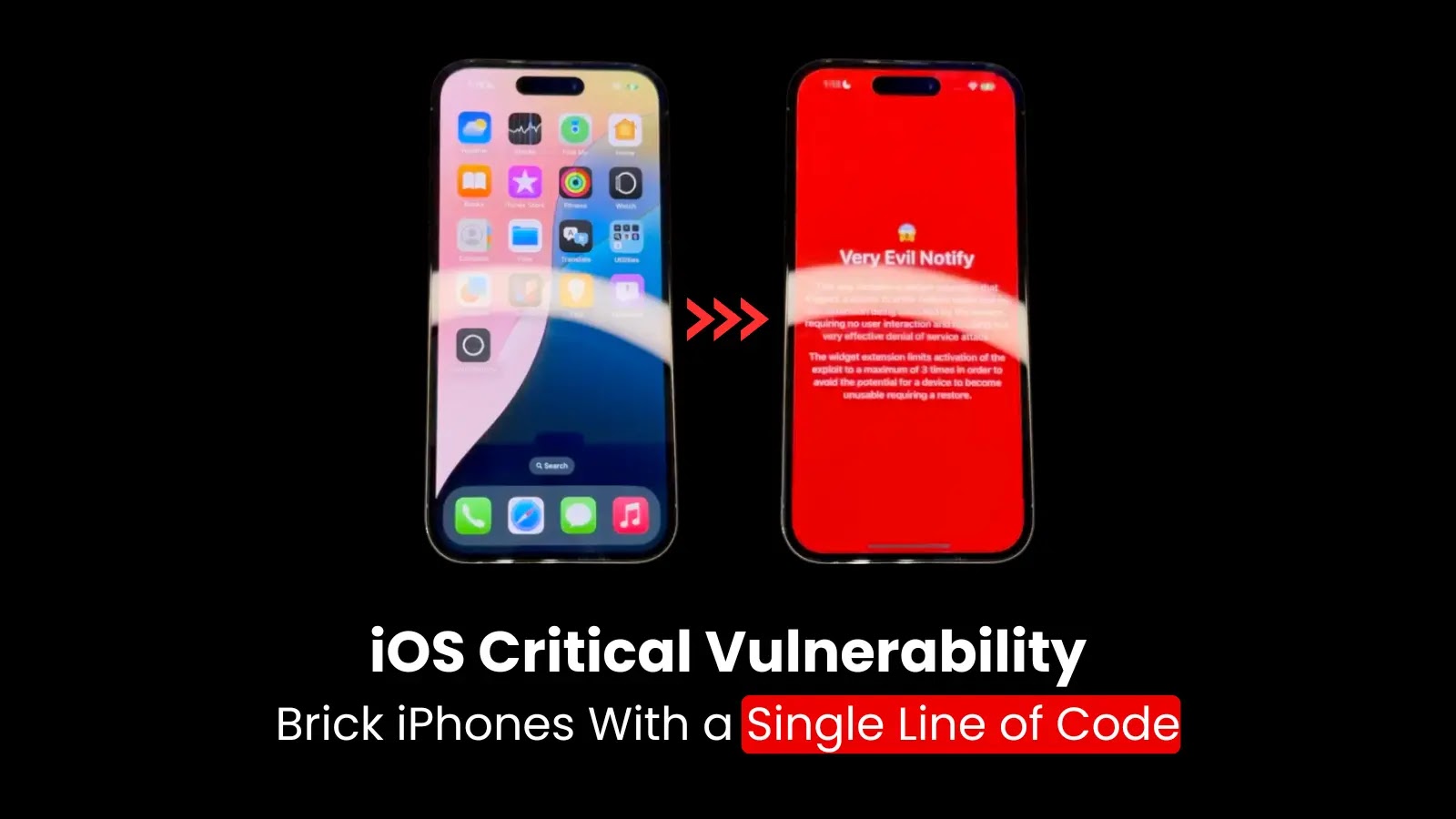
A critical vulnerability in iOS could allow malicious applications to disable iPhones with just a single line of code permanently….
Security researchers at Shelltrail have discovered three significant vulnerabilities in the IXON VPN client that could allow attackers to escalate…
As businesses and individuals increasingly rely on cloud services for storage, collaboration, and computing power, the importance of securing cloud…
Ransomware attacks are becoming more refined and pervasive, posing significant challenges to organizations globally. A Veeam report reveals that while…
Sam Altman has long been a key figure shaping the conversation around artificial intelligence. As the CEO of OpenAI and…
Cybercriminals have begun openly marketing a powerful new variant of the HiddenMiner malware on underground dark web forums, raising alarms…
Chinese products have become a staple in markets around the world. From household items like pens to complex machinery such…
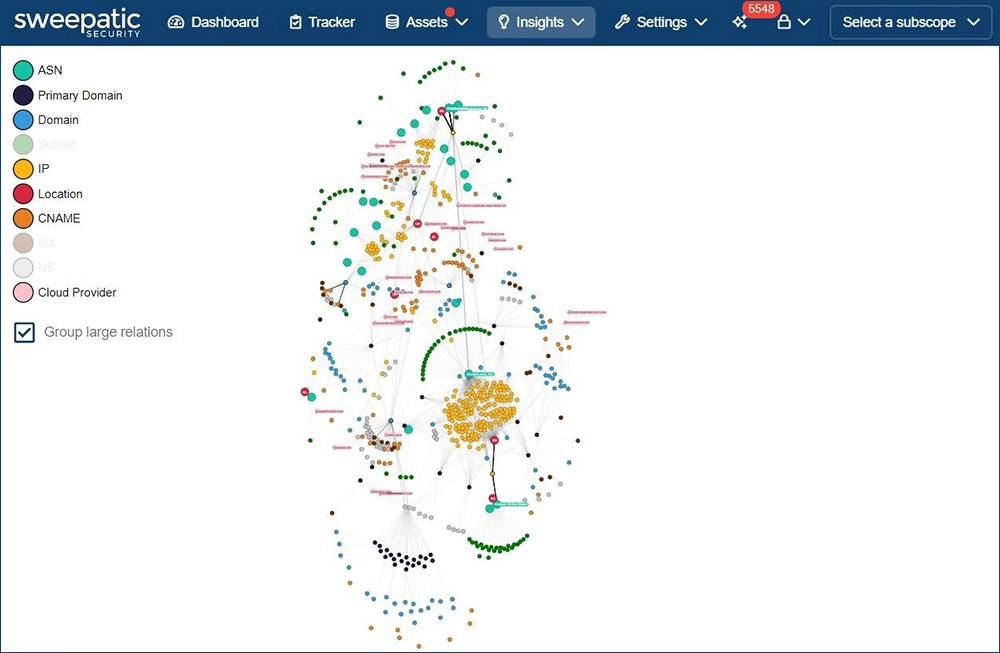
In a world where organizations’ digital footprint is constantly changing and attackers regularly capitalize on security failings in exposed IT…
Jeffrey Bowie, CEO of cybersecurity firm Veritaco, was arrested on April 14, 2025, facing two counts of violating Oklahoma’s Computer…
Jeffrey Bowie, the CEO of a local cybersecurity firm, has been arrested for allegedly planting malware on computers at SSM…
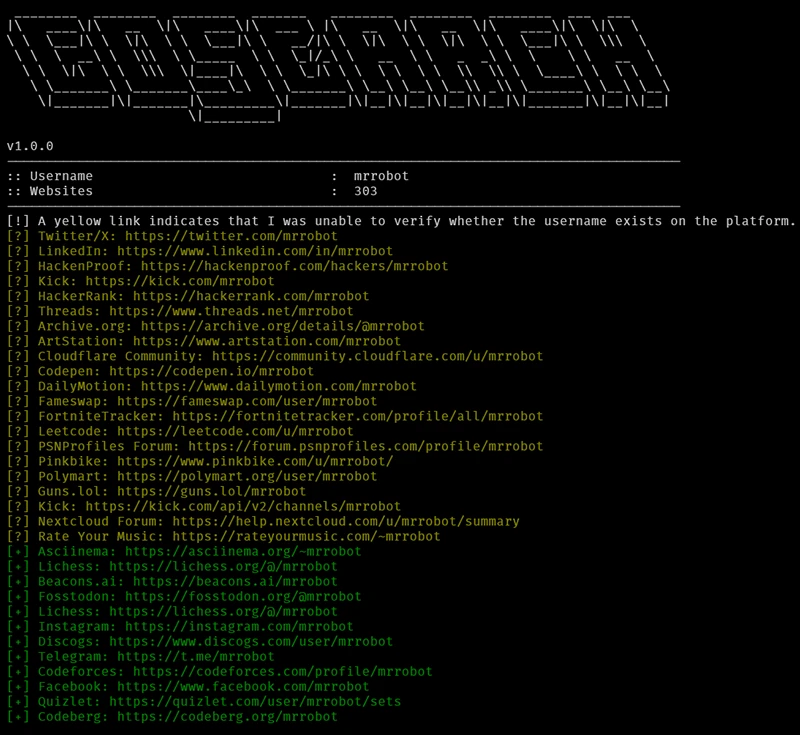
GoSearch is an open-source OSINT tool built to uncover digital footprints linked to specific usernames. Designed for speed and accuracy,…