On the morning of May 20, 2025, Kettering Health, a major Ohio-based healthcare provider operating 14 medical centers and over…
It seems not a day goes by without news of another crypto scam targeting unsuspecting holders. Those owning popular cryptocurrencies…
After watching the documentary “We Live in Public,” a hyperventilated account of the rise and weird fall of the dot-com…
With an exploit for a critical Roundcube vulnerability (CVE-2025-49113) being offered for sale on underground forums and a PoC exploit…
Jun 09, 2025The Hacker News You don’t need a rogue employee to suffer a breach. All it takes is a…
More than 7,000 people have received over £1bn between them as part of the government’s promise to provide financial redress…
OpenAI bans ChatGPT accounts linked to Russian, Chinese cyber ops Pierluigi Paganini June 09, 2025 OpenAI banned ChatGPT accounts tied…
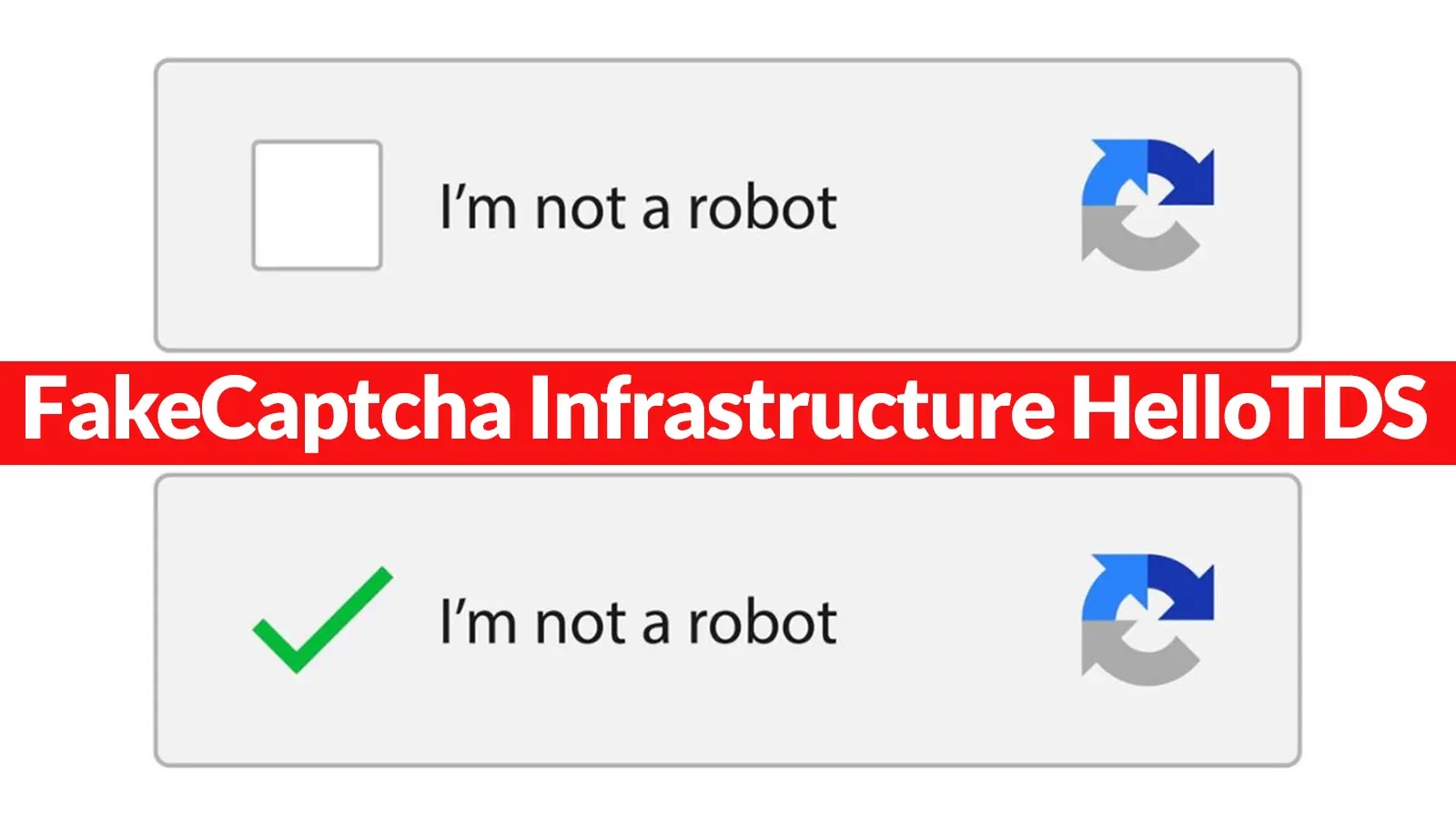
In recent months, a new wave of sophisticated malware campaigns has swept through millions of devices worldwide, driven by an…
A new Remote Access Trojan (RAT) named DuplexSpy has surfaced, posing a significant threat to Windows-based systems worldwide. Developed in…
Tel Aviv, Israel, June 9th, 2025, CyberNewsWire Available to the public and debuting at the Gartner Security & Risk Management…
London Tech Week 2025 has kicked off with a set of initiatives to bolster the UK’s sovereign artificial intelligence (AI)…
American infrastructure is powered by open-source software and no one knows who wrote it. That’s not hyperbole. It’s a structural…