The number of cybersecurity-related merger and acquisition (M&A) announcements surged in May 2025, with 42 deals. An analysis conducted by…
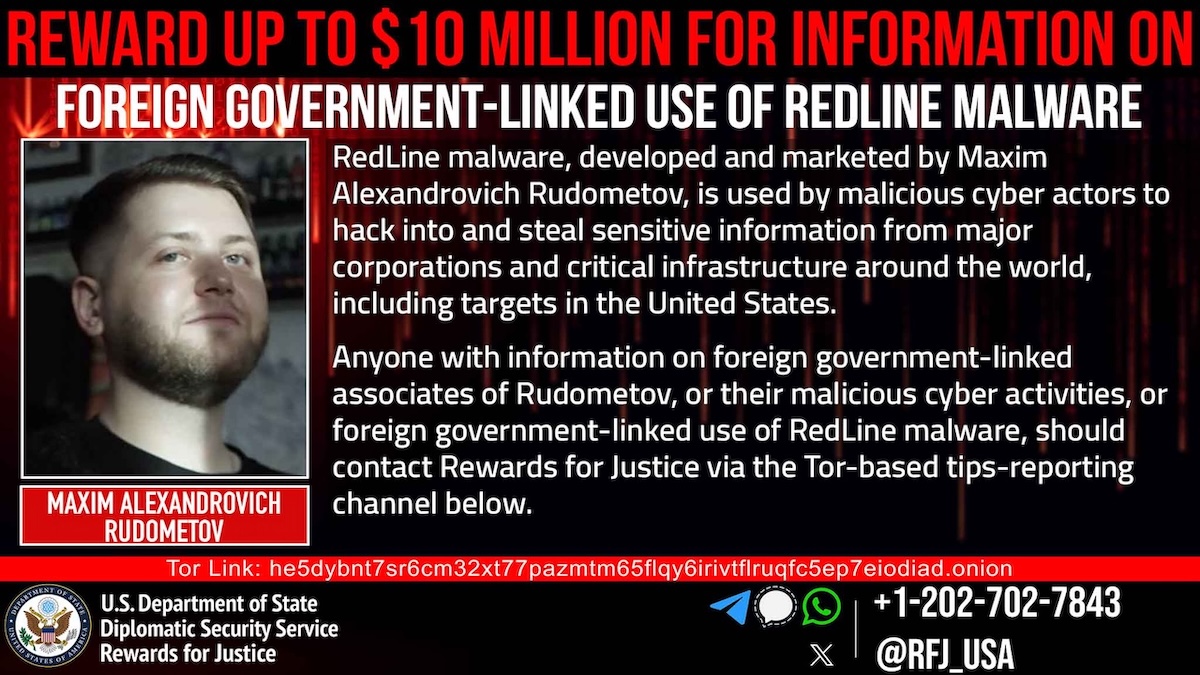
The United States Department of State’s Rewards for Justice program has announced a substantial bounty of up to $10 million…
In May 2025, AWS disclosed a critical remote code execution (RCE) vulnerability, CVE-2025-4318, in the @aws-amplify/codegen-ui package—a core dependency for…
The UK Information Commissioner’s Office (ICO) has launched an artificial intelligence (AI) and biometrics strategy, which the regulator says will…
The US Department of State, through its Rewards for Justice program, is offering a reward of up to $10 million…
U.S. Offers $10M bounty for info on RedLine malware creator and state hackers Pierluigi Paganini June 06, 2025 The U.S….
Government agencies worldwide are facing an unprecedented wave of cyberattacks, with adversaries employing advanced tactics to breach critical infrastructure and…
Jun 06, 2025The Hacker NewsCyber Resilience / Penetration Testing Cybersecurity involves both playing the good guy and the bad guy….
Data loss prevention (DLP) provider MIND this week announced raising $30 million in Series A funding, which brings the total…
Hewlett-Packard Enterprise (HPE) has released a critical security bulletin addressing multiple high-impact vulnerabilities in its Insight Remote Support (IRS) software,…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has released seven new ICS advisories, each highlighting cybersecurity vulnerabilities in key…
Russian threat actors are once again targeting Ukraine’s critical infrastructure with destructive malware, a fresh report from Cisco Talos shows….