Microsoft announced an increase in bug bounty payouts to $30,000 for AI vulnerabilities found in Dynamics 365 and Power Platform…
Priority number one for cybersecurity leaders across small-to-medium enterprises (SMEs) and managed service providers (MSPs) is to ensure IT environments…
The FBI (Federal Bureau of Investigation), the United States’ premier law enforcement agency, has recently published its Internet Crime Report…
Blue Shield of California leaked the personal data of 4.7 million people to Google after a Google Analytics misconfiguration. The…
Organisations using VMware now have no choice but to buy an annual subscription for a bundled product if they plan…
AI creating/debugging an exploit for the recent Erlang/OTP SSH vuln, map visualization and firewall for AWS activity, a multi-stage attack…
Page not found Unfortunately the page that you requested does not exist. Don’t worry, though, we have some great suggestions…
Got an Android phone? Got a tap-to-pay card? Then you’re like millions of other users now at risk from a…
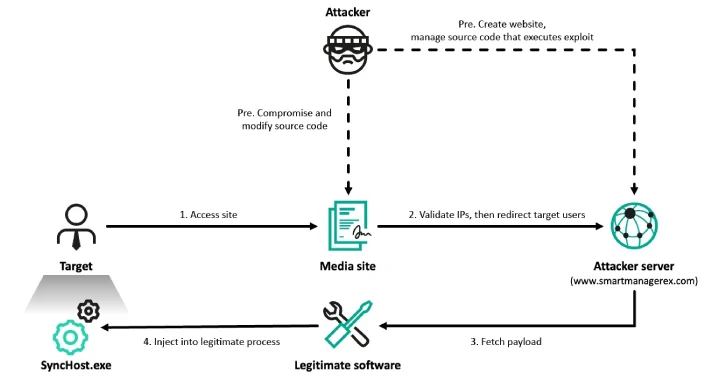
Apr 24, 2025Ravie LakshmananMalware / Threat Intelligence At least six organizations in South Korea have been targeted by the prolific…
Contactless payments and click-and-collect at Marks and Spencer (M&S) remain unavailable 72 hours after a cyber security incident at the…
Yale New Haven Health (YNHHS) is warning that threat actors stole the personal data of 5.5 million patients in a…
NVIDIA has issued an urgent security advisory addressing three high-severity vulnerabilities in its NeMo Framework, a platform widely used for…





![[tl;dr sec] #276 – AI-created PoC Exploit, Cloud Snitch, Kubernetes Attack Simulation [tl;dr sec] #276 - AI-created PoC Exploit, Cloud Snitch, Kubernetes Attack Simulation](https://image.cybernoz.com/wp-content/uploads/2025/04/tldr-sec-276-AI-created-PoC-Exploit-Cloud-Snitch-Kubernetes.png)