WhatsApp introduces Advanced Chat Privacy to protect sensitive communications Pierluigi Paganini April 24, 2025 WhatsApp adds Advanced Chat Privacy feature…
A critical remote code execution (RCE) vulnerability, identified as CVE-2025-3248 with a CVSS score of 9.8, has been uncovered in…
The Cybersecurity and Infrastructure Security Agency (CISA), a key agency responsible for protecting the United States’ critical infrastructure, has taken…
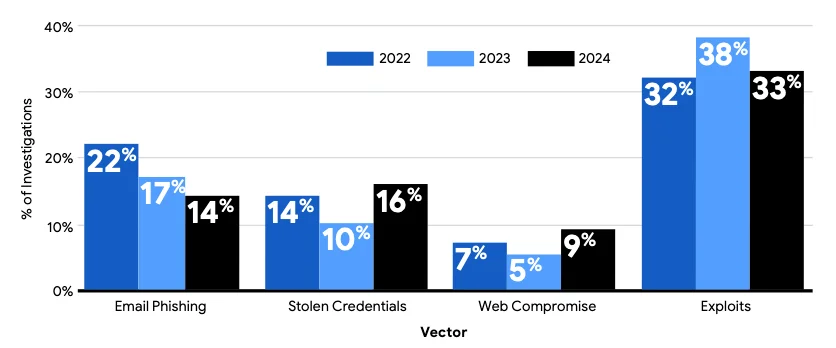
Mandiant has released the M-Trends 2025 report, which outlines global cyber attack trends based on their own incident response engagements…
SonicWall has disclosed a critical security vulnerability in its SSLVPN service that allows unauthenticated remote attackers to crash affected firewall…
A high-severity denial-of-service (DoS) vulnerability in Redis, tracked as CVE-2025-21605, allows unauthenticated attackers to crash servers or exhaust system memory by…
Swimlane announced Compliance Audit Readiness (CAR) Solution, designed to streamline compliance management and accelerate audit readiness. Powered by the Swimlane…
Daniele Tonella, global head of IT at ING Bank, tells Computer Weekly about his first nine months in the job,…
The Baltimore City Public Schools system has confirmed a cybersecurity incident that compromised the personal information of certain individuals associated…
Phishing campaigns have evolved significantly in 2025, with threat actors increasingly leveraging unconventional file formats to bypass security solutions. A…
Google’s Mandiant team has released its M-Trends 2025 report, highlighting the increasing sophistication of threat actors, particularly China-nexus groups. These…
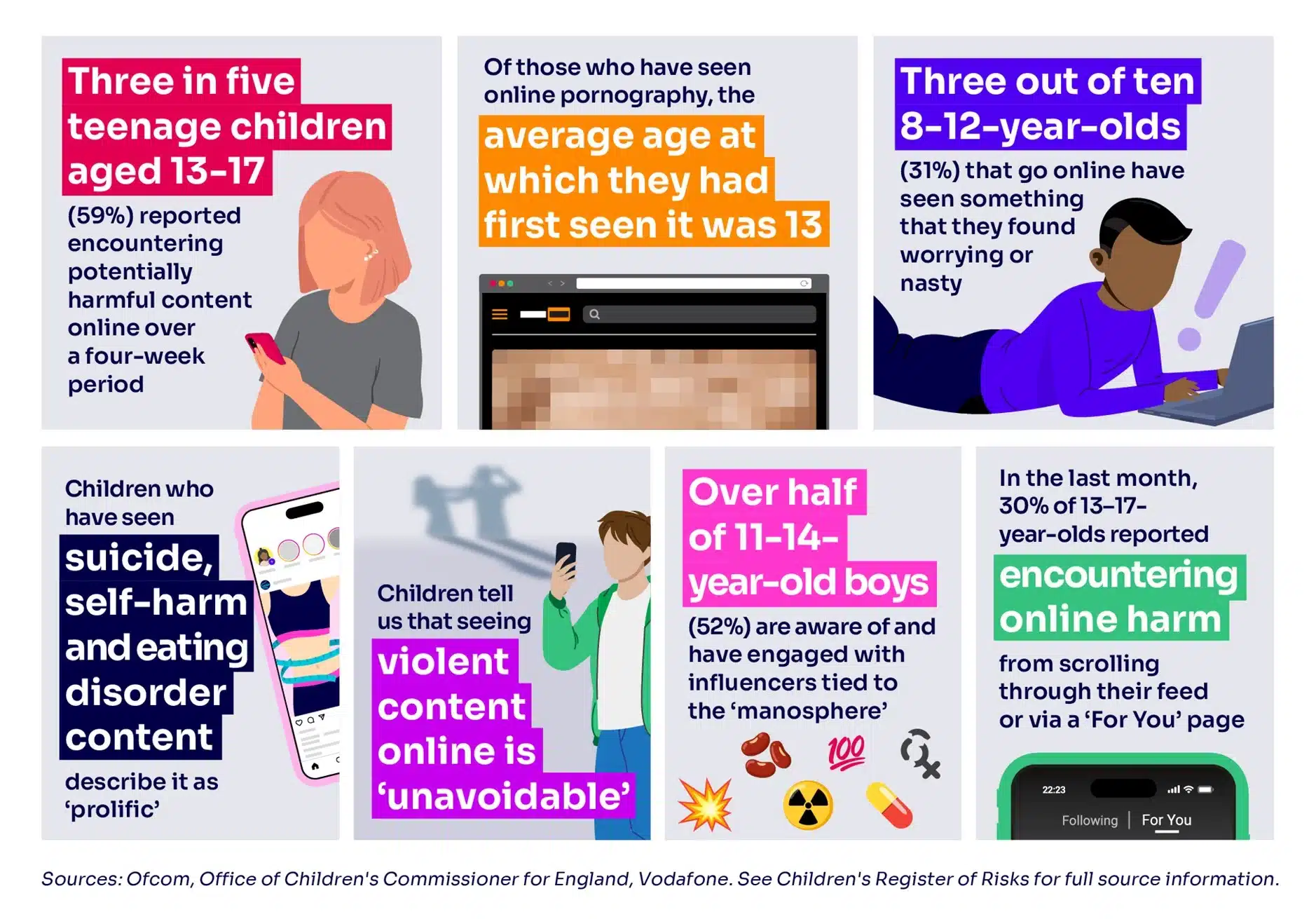
The United Kingdom communications regulator Ofcom has finalized a comprehensive set of child safety rules under the Online Safety Act,…