Microsoft has launched an expanded bug bounty program offering rewards of up to $30,000 for researchers who identify critical vulnerabilities…
Why Application Security is Non-Negotiable The resilience of your digital infrastructure directly impacts your ability to scale. And yet, application…
Blue Shield of California has disclosed a significant data breach affecting 4.7 million members, representing the majority of its nearly…
SonicWall has issued an urgent advisory (SNWLID-2025-0009) warning of a high-severity vulnerability in its SSLVPN Virtual Office interface that enables…
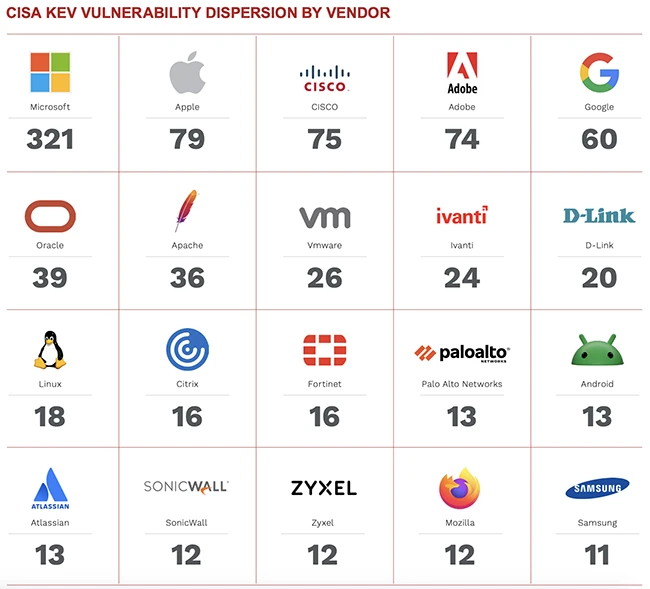
The Edgescan 2025 Vulnerability Statistics Report offers a data-rich snapshot of the global cybersecurity landscape, drawing from thousands of assessments…
On a month-by-month basis, recorded ransomware attacks dropped by 32% in March 2025, to 600 in total, according to NCC…
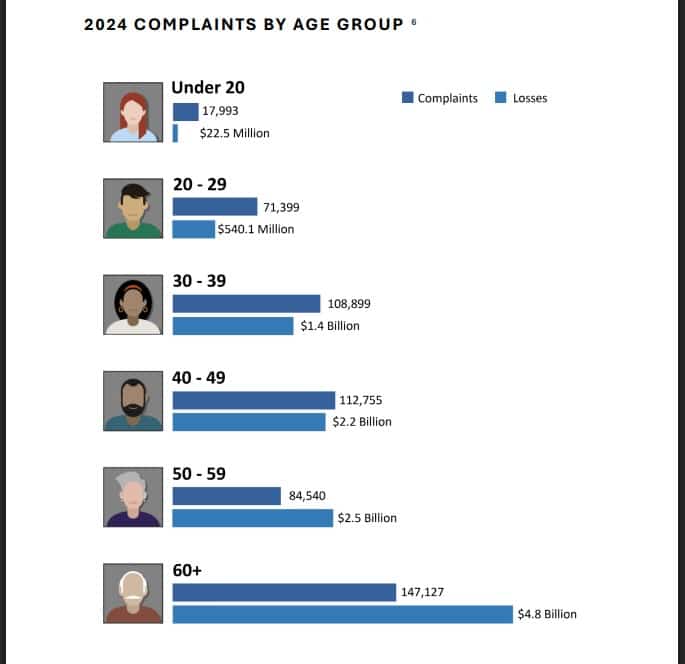
The Federal Bureau of Investigation (FBI) has released its latest Internet Crime Report for 2024, revealing a steep rise in…
In an era where cyber threats evolve faster than regulatory frameworks, Vice Presidents (VPs) of Security are redefining their roles…
Microsoft has launched a new bounty program that offers up to $30,000 to security researchers who discover vulnerabilities in its…
A significant increase in suspicious scanning activity targeting Ivanti Connect Secure (ICS) and Ivanti Pulse Secure (IPS) VPN systems, signaling…
Blue Shield of California has disclosed a significant data privacy incident affecting up to 4.7 million members, after discovering that…
While AI adoption is widespread, its impact on productivity, trust, and team structure varies sharply by role and region, according…