Despite billions spent annually on cybersecurity technology, organizations continue to experience breaches with alarming frequency. The most sophisticated security systems…
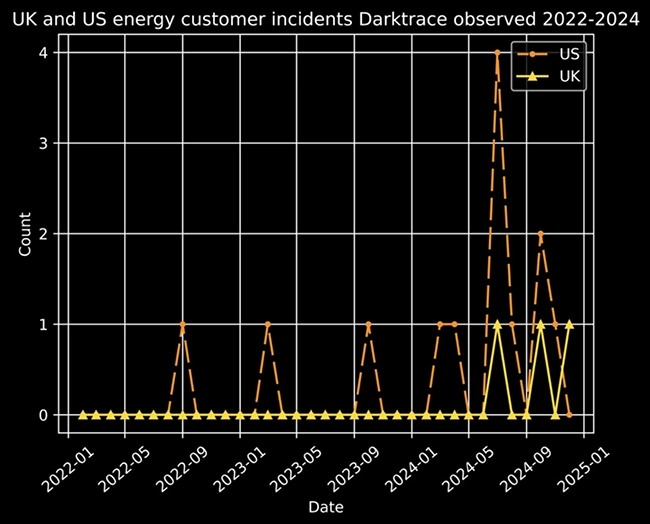
Cyber threats targeting the energy sector come in many forms, including state-sponsored actors seeking to disrupt national infrastructure, cybercriminals motivated…
Autism Spectrum Australia (Aspect) has improved its hiring effectiveness by implementing a new talent acquisition system and transforming its recruitment…
Launch of COGNNA at RSA 2025 Security teams today face an unstoppable challenge—one that isn’t just about technology but about…
Artificial Intelligence for Cybersecurity is a practical guide to how AI and machine learning are changing the way we defend…
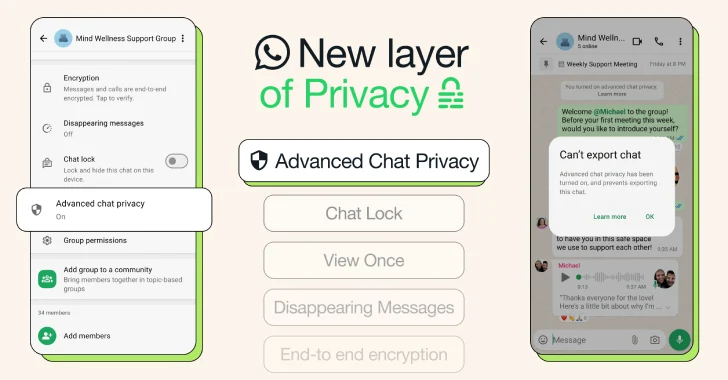
Apr 24, 2025Ravie LakshmananData Protection / Artificial Intelligence WhatsApp has introduced an extra layer of privacy called Advanced Chat Privacy…
Macquarie Bank is looking to AI to reduce the “cognitive load” on customers when it comes to managing their financial…
Have you ever heard the saying, “Better the devil you know than the devil you don’t”? In short, it’s better…
The ACT Public Service has kicked off a three-year modernisation of its core human resources and payroll technology is underway,…
A significant security vulnerability (CVE-2025-34028) has been discovered in Commvault Command Center Innovation Release, enabling unauthenticated attackers to execute arbitrary…
The relationship between an insurance provider and the insured is often described as adversarial: one party reluctantly pays a premium,…
WhatsApp has announced the rollout of its new “Advanced Chat Privacy” feature, designed to give users greater control over the…