Security researchers have demonstrated a non-invasive method to bypass Microsoft BitLocker encryption on Windows devices in just five minutes without…
Nova Scotia’s largest electric utility, Nova Scotia Power, has confirmed that customer information was stolen in a recent cyberattack that…
The Japanese government has set an ambitious target to increase the number of cybersecurity experts to 50,000 by 2030. This initiative…
A critical vulnerability in Microsoft’s BitLocker full disk encryption, demonstrating that it can be bypassed in under five minutes using…
Google has rolled out a fresh Stable Channel update for the Chrome browser across desktop platforms, including Windows, Mac, and…
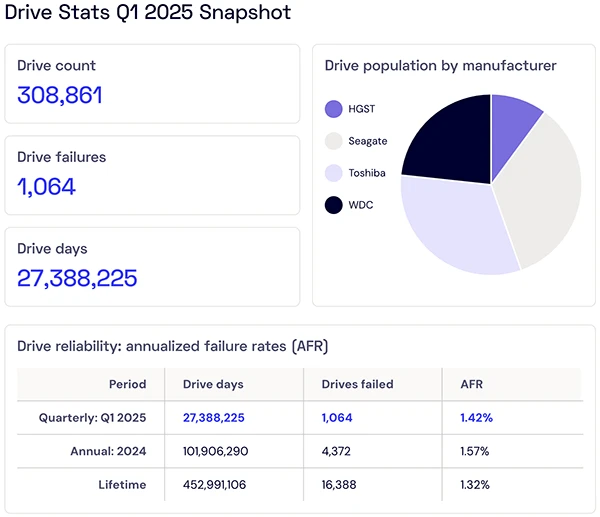
Cloud storage company Backblaze has released its Q1 2025 hard drive reliability report, which provides insights into the performance and…
May 15, 2025Ravie LakshmananBrowser Security / Web Security Google on Wednesday released updates to address four security issues in its…
In AI, as with so many advancing technologies, security often lags innovation. The xAI incident, during which a sensitive API…
A newly discovered malicious Python package, solana-token, has been weaponized to steal source code and sensitive secrets from developers working…
Google Issues Warning to U.S. Retailers About the Growing Threat of Scattered Spider Cyberattacks Google’s Threat Intelligence team has issued…
In this Help Net Security interview, Anne Sofie Roed Rasmussen, CISO at Novonesis, discusses how a science-driven organization approaches cybersecurity,…
The Blockchain Security Standards Council (BSSC) launched its first four security standards, marking a significant milestone in the journey towards…