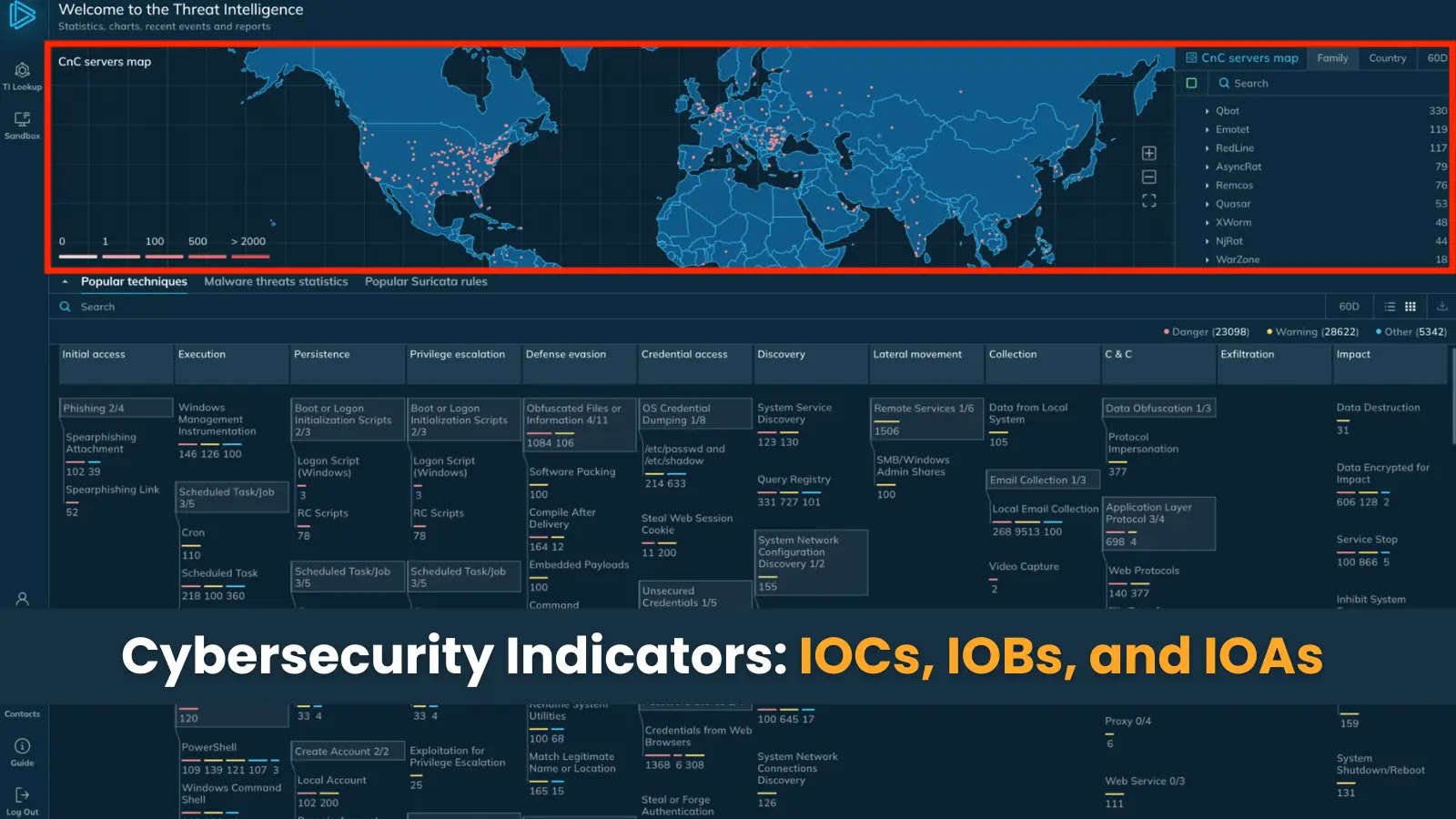
In Cybersecurity indicators, three powerful tools Indicators of Compromise (IOCs), Indicators of Behavior (IOBs), and Indicators of Attack (IOAs) are…
VCC or virtual client computing is an advanced IT approach with a comprehensive application and desktop virtualization solution. The system is fabricated…
Small and midsized businesses (SMBs) continue to be prime targets for cybercriminals, with network edge devices playing a critical role…
54% of tech hiring managers say their companies are likely to conduct layoffs within the next year, and 45% say…
Many conservatives and libertarians are deeply confused about the morality of markets. They view markets as pure and benign forces…
The future of the federal government’s software-security advocacy campaign is in doubt following the departure of the two Cybersecurity and…
IBM X-Force observed an identical breakdown of the top methods cybercriminals used to intrude networks for two years running, the…
A proof-of-concept attack called “Cookie-Bite” uses a browser extension to steal browser session cookies from Azure Entra ID to bypass multi-factor…
In today’s rapidly evolving threat landscape, Chief Information Security Officers (CISOs) face the challenge of securing their organizations with finite…
First, there was phishing. The goal: To trick targets into revealing information or completing unauthorized actions. Around since the 1990s,…
Hackers are now exploiting a legitimate Microsoft utility, mavinject.exe, to inject malicious DLLs into unsuspecting systems. This utility, intended for…
This week on the Lock and Code podcast… If you don’t know about the newly created US Department of Government…