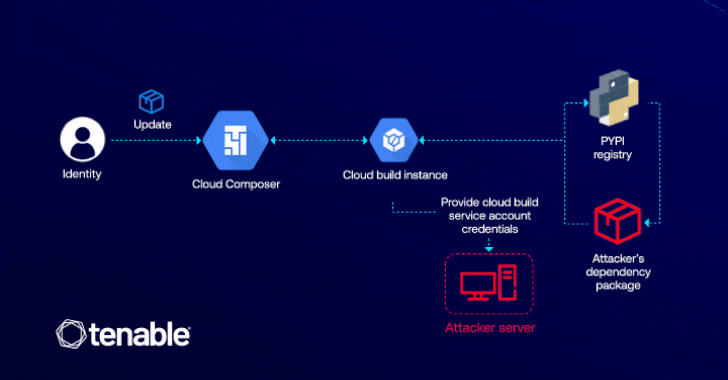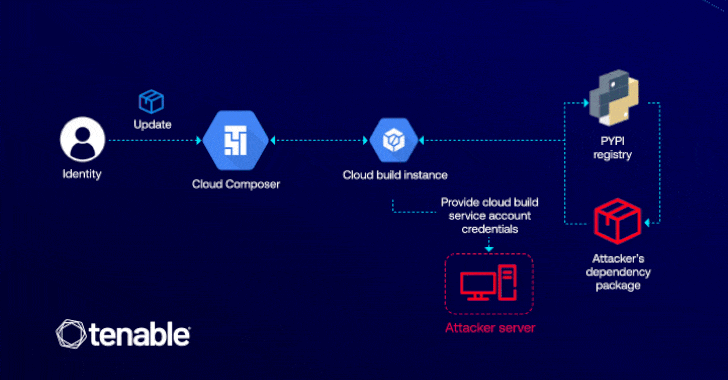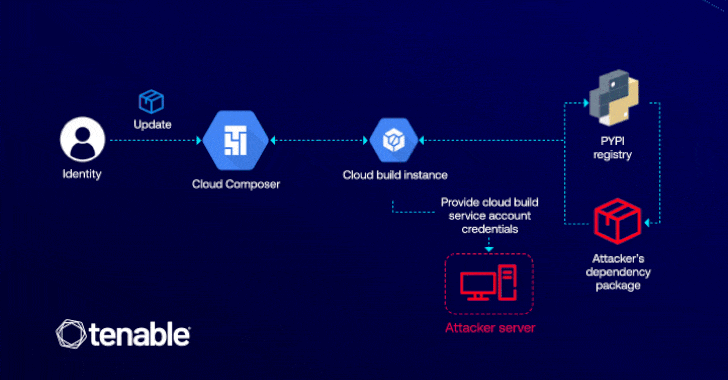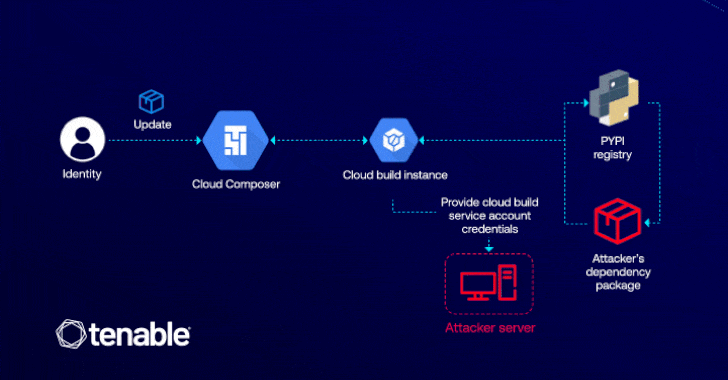
Cybersecurity researchers have detailed a now-patched vulnerability in Google Cloud Platform (GCP) that could have enabled an attacker to elevate…
I’ve always been taught it’s polite to trim emails and type the reply below the text I’m responding to: Because…
In a concerning development for the open-source community, several malicious packages on npm and PyPI repositories have been discovered posing…
Delivering Security Without Complexity in an Era of Sophisticated Cyber Threats Let’s face it—today’s cybersecurity landscape is a battlefield. Ransomware…
Joining Criminal IP at Booth S-634 | South Expo, Moscone Center | April 28 – May 1, 2025 Criminal IP,…
Terrance, United States / California, April 22nd, 2025, CyberNewsWire Joining Criminal IP at Booth S-634 | South Expo, Moscone Center…
Cybercriminals are abusing Google’s infrastructure, creating emails that appear to come from Google in order to persuade people into handing…
In 2024, the National Cyber Security Centre (NCSC) celebrated a decade of its baseline cyber security certification, Cyber Essentials (CE)….
Everyone knows smart people read and lazy people watch TV, but aren’t they often doing the same thing? I’m reading…
As organizations accelerate their digital transformation journeys, the Chief Information Security Officer (CISO) role has never been more pivotal or…
Beyond Silos By Dan Cole, VP of Product Marketing, ThreatConnect We know that attackers are outpacing defenders: we’ve all heard…
Why Application Security is Non-Negotiable The resilience of your digital infrastructure directly impacts your ability to scale. And yet, application…