A newly disclosed VMware Tools vulnerability could enable attackers with limited access to compromise virtual machines (VMs). Broadcom, which owns…
Moldovan Police arrested a 45-year-old foreign man participating in ransomware attacks on Dutch companies Pierluigi Paganini May 13, 2025 A…
Scattered Spider, also known as Roasting 0ktapus and Scatter Swine, has emerged as a formidable threat actor targeting UK retail…
Fortune reports Sal Sferlazza and Christopher Matarese co-founders of Austin, Texas-based NinjaOne, recently announced $500 million in Series C extensions at a $5…
The North Korea-linked threat actor known as Konni APT has been attributed to a phishing campaign targeting government entities in…
The government’s Gov.uk One Login digital identity system has lost its certification against the government’s own trust framework for digital…
Jamf Threat Labs has identified a novel macOS infostealer that exploits PyInstaller, a legitimate open-source tool used to bundle Python…
May 13, 2025The Hacker NewsAI Security / Zero Trust The cybersecurity landscape has been dramatically reshaped by the advent of…
The faulty system at the heart of the Post Office Horizon scandal could still be in use in Post Office…
In a significant cybersecurity investigation, researchers have revealed an elaborate fraud scheme orchestrated by North Korean nationals who used stolen…
A newly identified information-stealing malware dubbed PupkinStealer has emerged as a significant threat to Windows users, with its first sightings…
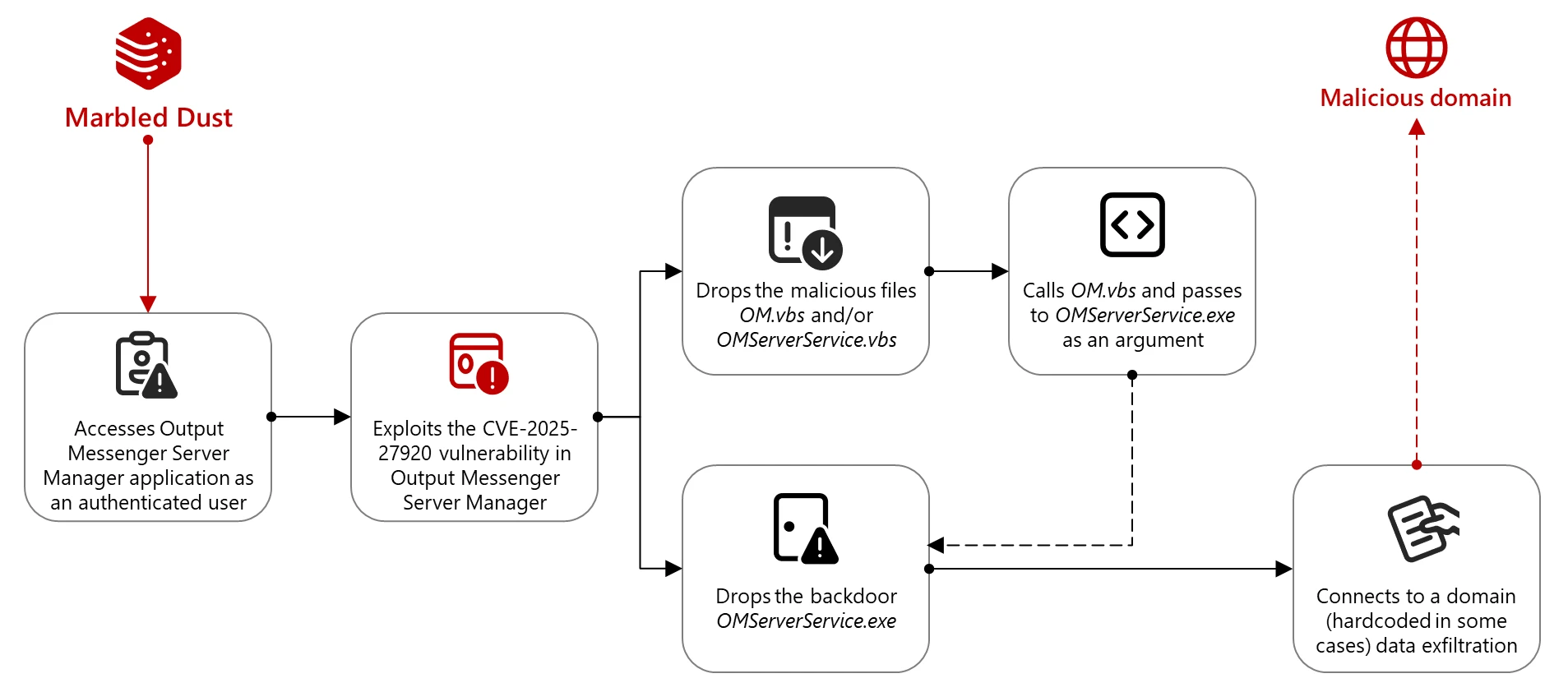
APT group exploited Output Messenger Zero-Day to target Kurdish military operating in Iraq Pierluigi Paganini May 13, 2025 A Türkiye-linked…