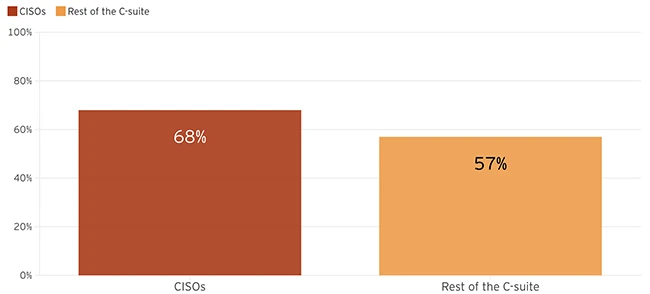
New research from EY US shows that cyber attacks are creating serious financial risks. C-suite leaders don’t always agree on…
Apr 22, 2025Ravie LakshmananCyber Espionage / Threat Intelligence The China-linked cyber espionage group tracked as Lotus Panda has been attributed…
But only temporarily. During the short period after reading Hitchens, say a couple of hours, or perhaps a few days,…
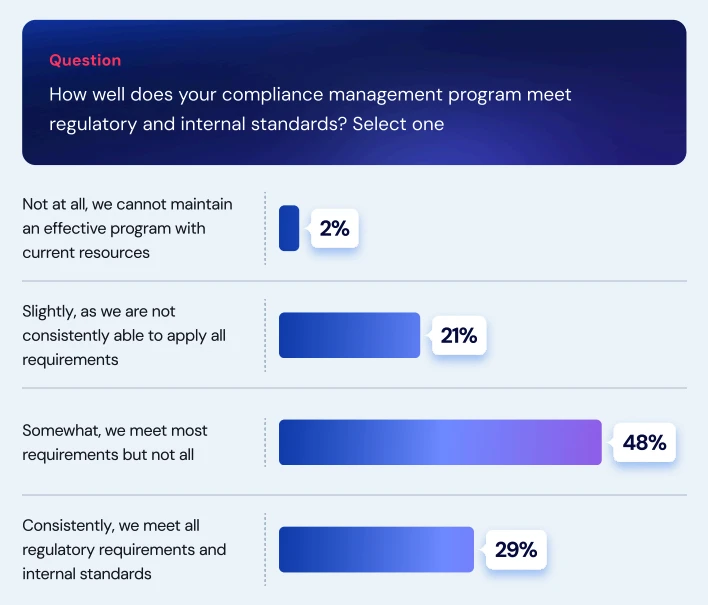
Only 29% of all organizations say their compliance programs consistently meet internal and external standards, according to Swimlane. Their report…
Remember during the election when we were all talking about who was fighting for what? Remember how Obama was claiming…
Libertarianism is attractive. I find that it functions as a sanctuary for both those unhappy with conservatism (which they often…
Cybersecurity researchers have discovered a critical vulnerability in WinZip that enables attackers to bypass Windows’ Mark-of-the-Web (MotW) security feature, potentially…
Many of us in the tech industry fancy ourselves experts on politics and various types of policy–especially taxation. We feel…
A security architect with the National Labor Relations Board (NLRB) alleges that employees from Elon Musk‘s Department of Government Efficiency…
I don’t believe men and women in relationships should spend significant amounts of time with people of the opposite sex….
Asian crime syndicates behind the multibillion-dollar cyberscam industry are expanding globally, including to South America and Africa, as raids in…
Work on that instead of new years resolutions. Anyway, enough with the good cheer. If you absolutely must do resolutions,…