In 2024, financial institutions around the globe suffered an average loss of $6.08 million due to ransomware attacks. This marked…
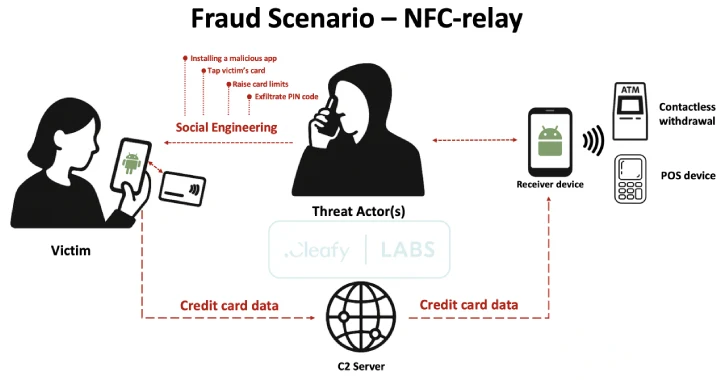
Apr 21, 2025Ravie LakshmananTechnology / Mobile Security A new Android malware-as-a-service (MaaS) platform named SuperCard X can facilitate near-field communication…
As a security consultant I do quite a bit of travel for my job. It’ssomething I enjoy immensely, but standing…
For enterprises, the cloud is no longer just an option; it’s a necessity. With 80% of businesses now viewing the public…
ClickFix attacks are gaining traction among threat actors, with multiple advanced persistent threat (APT) groups from North Korea, Iran, and…
As organizations gear up for 2025, third-party risk management (TPRM) remains a top priority. The need to manage risks associated…
In today’s rapidly evolving threat landscape, Chief Information Security Officers (CISOs) are tasked with more than just deploying the latest…
Morphisec discovers a new malware threat ResolverRAT, that combines advanced methods for running code directly in computer memory, figuring out…
If you enjoy the command line then you don’t need to be sold on efficiency or purity of action. But…
In a rather clever attack, hackers leveraged a weakness that allowed them to send a fake email that seemed delivered…
Recent research has unveiled a concerning vulnerability within the realm of containerized applications, where threat actors are leveraging stolen certificates…
Both the left and the right talk about the health of the middle class as a key indicator of American…