In today’s rapidly evolving threat landscape, the resilience of perimeter security is continuously being put to the test by the…
Linus Torvalds announced the release of Linux 6.15-rc3, delivering a fresh batch of bug fixes and minor adjustments to the…
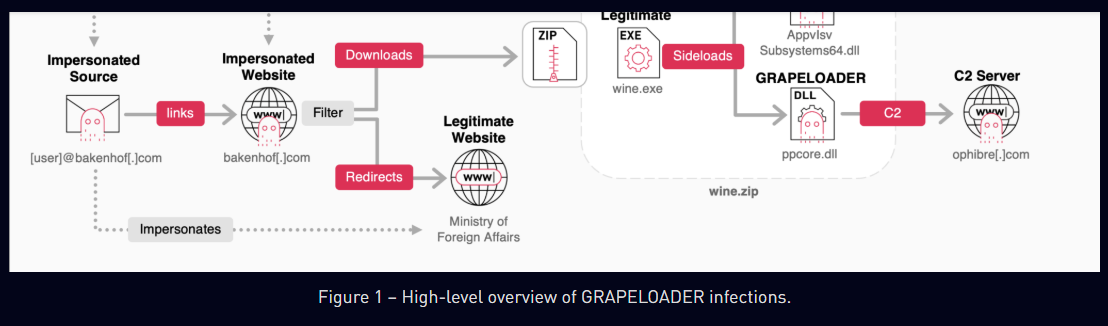
Russia-linked APT29 targets European diplomatic entities with GRAPELOADER Pierluigi Paganini April 21, 2025 Russia-linked group APT29 targeted diplomatic entities across…
Attended a ton of great talks that will get parsed into additions to our testing methodologies Had valuable face time…
A newly uncovered hacking campaign is targeting business leaders and cryptocurrency firms by abusing Zoom’s remote control feature, allowing attackers…
Oracle has released version 8 of its Unbreakable Enterprise Kernel (UEK), a custom Linux kernel built for Oracle Linux. UEK…
Apr 21, 2025Ravie LakshmananVulnerability / Threat Intelligence Cybersecurity researchers have disclosed a surge in “mass scanning, credential brute-forcing, and exploitation…
Ahold Delhaize USA, the parent company of several well-known American supermarket brands, has confirmed that data was stolen during a…
Smart, educated people tend to avoid junk food. They tend to be thinner and have better diets because they’re simply…
A major security flaw in the Speedify VPN application for macOS, tracked as CVE-2025-25364, has exposed millions of users to the…
April 18, 2025 – Text scams come in many forms and are an ever increasing threat doing an awful lot…
I already did a post on my recent Vegas trip, but there’s a piece of it that I didn’t mention….