Businesses are losing out on an average of $98.5 million a year as a consequence of cyber threats, fraud, regulatory…
Hi $NAME, Basically, the role of the government is to provide for our welfare, to see that we flourish, etc….
It seems to me that every time I come across real philosophers they have an extremely pompous view of non-academic,…
I am demoing a Samsung Galaxy S III. It’s the new flagship Android device, and I like a lot about…
I’ve been thinking a lot recently about the habits of productive people. When I say productive I mean successful–as in…
This week on the Lock and Code podcast… If you don’t know about the newly created US Department of Government…
I have a friend who is getting into OS X for the first time after being a lifetime poweruser in…
I apologize for being so late to the game here, but aren’t the Buddhist concepts of Karma and the inevitable…
Neil deGrasse Tyson (our generation’s Carl Sagan) takes what appears to be intellectual high ground by denying that the term…
For most of human history people have been wrong about Earth’s place in the universe. Some thought we were the…
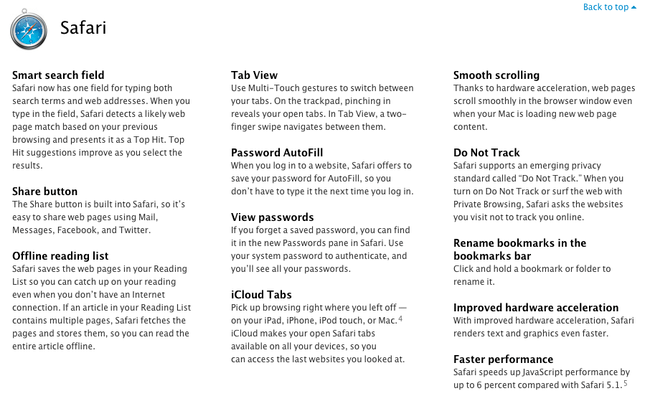
With the changes to Safari coming up in Mountain Lion I may abandon Chrome as my primary browser. Here are…
I realized recently that I value most those who are able to step outside convention when living their lives. The…