Before going into my qualms with Daniel Dennett’s capability/evitibility-based free will, I want to point out that most supporters of…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Apple plugs zero-day holes used…
When open allocation is in play, projects compete for engineers, and the result is better projects. When closed allocation is…
I think a lot about customer service. Or, what I really mean is that I get angry a lot about…
This is an essay about being productive to the world around you. Confused, you say, “How does any of that…
There’s some phenomenal password research here from clarkson.edu that talks about common passwords found during Internet attacks. I’ve taken those…
The Russian state-sponsored threat actor known as APT29 has been linked to an advanced phishing campaign that’s targeting diplomatic entities…
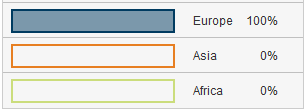
Or, at least according to 23andMe. When they show racial breakdowns they only show three categories: African, European, and Asian….
A while back I posted about having experiences through books. I was thinking again about this today and was imagining…
When Ruma*, a graduate student in South Korea, received sexually explicit doctored images of herself via Telegram in 2021, she…
America is wide open and trusting. This shouldn’t change. The idea of stopping terrorist attacks from occurring is simply asinine…
I am quite curious how top tier writers square the circle of Strunk and White’s demand for being concise and…