Attackers exploited SonicWall SMA appliances since January 2025 Pierluigi Paganini April 19, 2025 Threat actors are actively exploiting a remote…
This will be rough. I’ve always been attracted to the idea of identifying unifying characteristics of desired society, and defining…
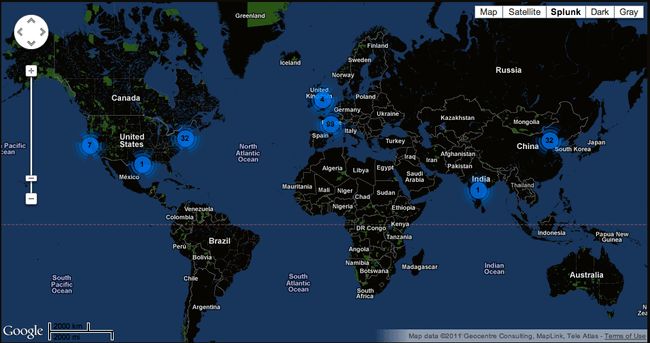
I never stop being fascinated by the fact that web admins have boxes online that anyone in the world can…
In a comprehensive analysis of the ransomware landscape in the first quarter of 2025, Microsoft Threat Intelligence has highlighted significant…
One of the most depressing things in life is not being able have all your friends from various phases of…
In a concerning development within the Android ecosystem, a new malware variant known as “Gorilla” has been identified, primarily targeting…
Apr 19, 2025Ravie LakshmananLinux / Malware Cybersecurity researchers have uncovered three malicious packages in the npm registry that masquerade as…
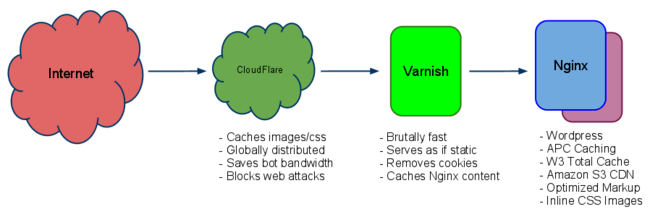
[ NOTE: I am now using Nginx for everything, i.e. not using Varnish anymore, and getting the same or better…
In today’s digital era, businesses are increasingly adopting cloud computing to store data, run applications, and manage infrastructure. However, as…
One of the things I worry about most is not being able to recall the great experiences that have happened…
In this week’s episode: Mason talks about AI powered spreadsheets! … it’s cooler than it sounds. Perry & Mason cover…
On this edition of CertByte, we discuss a question from N2K’s Cisco® Certified Network Associate (CCNA) practice test. As your…