May 09, 2025Ravie LakshmananVulnerability / Industrial Security A China-linked unnamed threat actor dubbed Chaya_004 has been observed exploiting a recently…
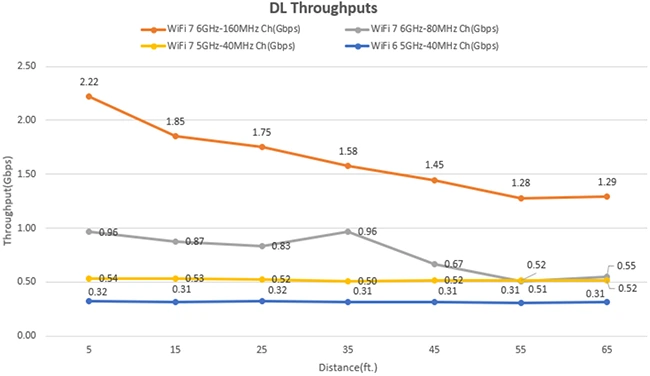
The next generation of wireless technology is getting a real-world test, and the results are promising. Recent trials led by…
Unitree Robotics, one of China’s leading robot manufacturers, said it shut down a third-party remote control service that had exposed…
The Cabinet Office is set to miss its targets for the UK government to be “cyber resilient” by the end…
Top executives at AI giants OpenAI, Microsoft and Advanced Micro Devices said at a US Senate hearing that while the…
The FBI warns that threat actors are deploying malware on end-of-life (EoL) routers to convert them into proxies sold on the…
US Customs and Border Protection (CBP) has quietly rescinded several internal policies that were designed to protect some of the…
Cloud-native applications offer scalable, automated workflows, intelligent data processing, and seamless deployments. However, many organizations still struggle to manage their…
The transformation needed for organisations in the UK to be ready for the threat of post-quantum computing will make preparations…
Apple has asked a US federal appeals court to temporarily pause key provisions in a US judge’s ruling that ordered…
An npm package named ‘rand-user-agent’ has been compromised in a supply chain attack to inject obfuscated code that activates a…
Google Chrome has emerged as the undisputed champion of data collection among 10 popular web browsers studied on the Apple…